by Robin Dost
Introduction
Much of my previous work has focused on understanding threat actors not through individual malware samples alone, but through infrastructure, operational behavior, and strategic intent. Over time, a recurring problem became increasingly difficult to ignore:
While our visibility into attacker tradecraft continues to improve, our ability to decide what to defend first often does not.
Most security frameworks excel at describing what exists, techniques, controls, and best practices, but remain largely silent on what should matter most when resources are limited or when a specific threat actor becomes relevant.
Instead of introducing another generic framework, this article applies an actor-centric prioritization methodology focused on attacker intent and impact.
This approach emerged from a practical need I repeatedly encountered: organizations often had technically sound controls in place, yet still failed to prevent strategic loss, because their defensive investments were misaligned with the attackers actual objectives.
Why ACDP Was Developed
Actor-Centric Defensive Prioritization (ACDP) was developed to address a persistent gap between threat intelligence and defensive decision-making.
Threat intelligence typically answers questions such as:
- Who is active?
- What techniques are being used?
Defensive planning, however, must answer differnt questions:
- What failure would be unacceptable?
- Which controls meaningfully disrupt this actors strategy?
In real world environments, especially those facing state-aligned or destructive actors, it is rarely feasible to implement every recommended control simultaneously.
Prioritization becomes inevitable.
ACDP exists to make that prioritization explicit, defensible, and actor-aware.
What Makes This Approach Different
ACDP does not attempt to replace established frameworks such as MITRE ATT&CK or NIST.
Instead, it operates one level above them, using their outputs as inputs.
Its defining characteristic is a deliberate shift in perspective:
- from technique coverage to strategic disruption
- from static maturity models to adaptive decision-making
- from generic best practices to context-driven trade-offs
The result is a reasoned ordering of defensive actions, based on how much they interfere with an adversary intent and how much damage they prevent if that interference fails.
Advantages of an Actor-Centric Approach
The strengths of ACDP are primarily practical:
- ACDP enables rapid reprioritization when threat actor relevance changes
- It aligns defensive investment with attacker objectives instead of abstract risk scores
- It acknowledges budget and operational constraints instead of assuming ideal conditions
- It helps explain why certain controls take priority, a critical factor in both technical and executive discussions
Most importantly: ACDP encourages organizations to think in terms of losing conditions, not only detection coverage
Limitations and Trade-Offs
ACDP is not without drawbacks.
Because it is actor-centric, its effectiveness depends on the quality of the underlying threat intelligence.
Incorrect assumptions about attacker intent can lead to misplaced priorities.
Additionally, ACDP does not provide prescriptive control definitions or implementation guidance. It assumes foundational security hygiene already exists and focuses solely on ordering, not designing, defensive measures.
Finally, ACDP deliberately avoids the comfort of exhaustive coverage. It forces uncomfortable decisions, choosing what not to prioritize, which may challenge existing security narratives.
A Practical Motivation
The motivation behind ACDP is operational necessity
In environments where time, budget, and certainty are constrained, security decisions must be made before all information is available. ACDP provides a structured way to make those decisions without pretending that all risks are equal.
If defensive priorities do not change when attacker intent changes, prioritization is no longer strategic
ACDP in Practice: Quantified Prioritization Example
This section demonstrates how ACDP produces concrete priorities, using a scoring example against Sandworm.
Step 0: Define the Objective Profile
Based on historical and current operations, Sandworm is modeled as a:
Destructive, state-aligned actor prioritizing strategic impact over access longevity
This assumption directly influences weighting.
Step 1: Define the Scoring Axes
Each defensive control is evaluated across four axes.
Axis A: Actor Disruption Value (ADV)
How strongly does this control interfere with the actors campaign strategy?
| Score | Meaning |
|---|---|
| 5 | Breaks or invalidates the strategy |
| 4 | Forces significant tradecraft change |
| 3 | Causes friction |
| 2 | Minor inconvenience |
| 1 | Negligible effect |
Axis B: Impact Risk Reduction (IRR)
How much real damage does this control prevent if the actor succeeds elsewhere?
| Score | Meaning |
|---|---|
| 5 | Prevents catastrophic / irreversible impact |
| 4 | Strongly limits blast radius |
| 3 | Partial damage reduction |
| 2 | Minimal reduction |
| 1 | Cosmetic |
Axis C: Cost & Operational Complexity (CC)
How realistic is implementation under time and budget pressure?
| Score | Meaning |
|---|---|
| 5 | Low cost, low friction |
| 4 | Moderate effort |
| 3 | Manageable complexity |
| 2 | High effort |
| 1 | Very expensive / disruptive |
Axis D: Detection-to-Decision Time (DDT)
Does this control provide usable signal early enough to change outcomes?
| Score | Meaning |
|---|---|
| 5 | Immediate / pre-impact |
| 4 | Early warning |
| 3 | Delayed but actionable |
| 2 | Mostly reactive |
| 1 | Post-incident only |
Step 2: Actor-Specific Weighting
For a destructive actor, impact prevention and strategic disruption dominate:
- ADV = 35%
- IRR = 35%
- CC = 15%
- DDT = 15%
Step 3: Scoring Selected Controls
Candidate Controls
- Immutable offline backups
- VPN / edge device inventory & patch SLAs
- Historical DNS & infrastructure analysis
- PowerShell command-line logging
- Scheduled task auditing
- Security awareness training
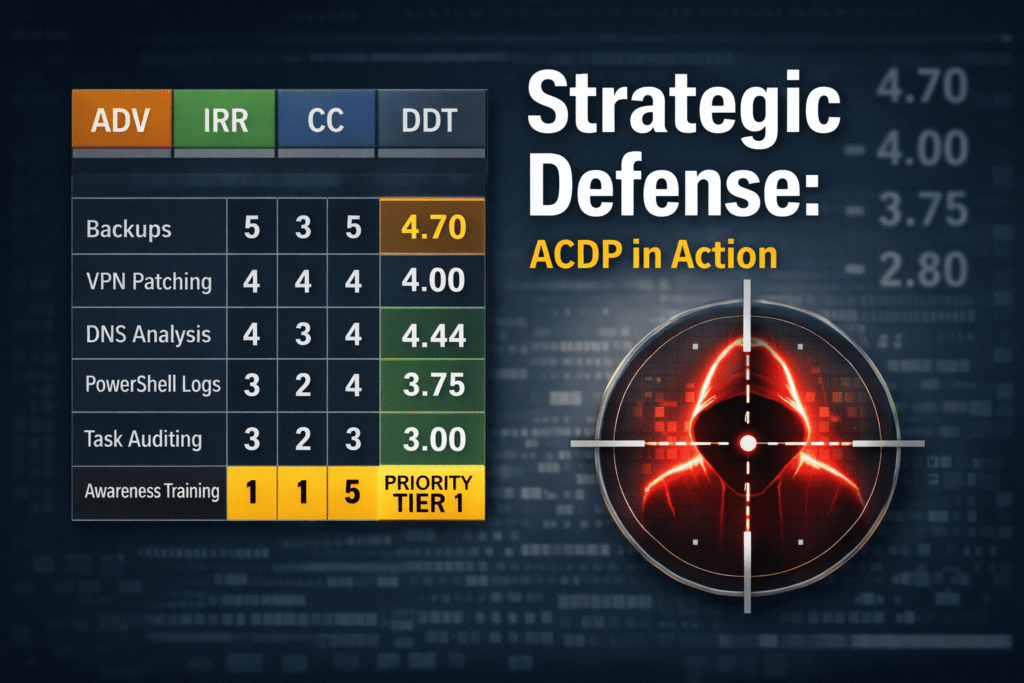
Scoring Table
| Control | ADV | IRR | CC | DDT |
|---|---|---|---|---|
| Immutable offline backups | 5 | 5 | 3 | 5 |
| Edge inventory & patching | 4 | 4 | 4 | 4 |
| Historical DNS analysis | 4 | 3 | 4 | 4 |
| PowerShell logging | 3 | 2 | 4 | 3 |
| Scheduled task auditing | 3 | 2 | 3 | 3 |
| Awareness training | 1 | 1 | 5 | 1 |
Step 4: Priority Index Calculation
Formula
PI = (ADV × 0.35) + (IRR × 0.35) + (CC × 0.15) + (DDT × 0.15)Example Calculations
Immutable offline backups
(5×0.35) + (5×0.35) + (3×0.15) + (5×0.15) = 4.70PowerShell logging
(3×0.35) + (2×0.35) + (4×0.15) + (3×0.15) = 2.80Step 5: Final Prioritization
| Control | PI | Priority Tier |
|---|---|---|
| Immutable offline backups | 4.70 | Tier 1 |
| Edge inventory & patching | 4.00 | Tier 1 |
| Historical DNS analysis | 3.75 | Tier 2 |
| PowerShell logging | 2.80 | Tier 2 |
| Scheduled task auditing | 2.75 | Tier 3 |
| Awareness training | 1.90 | Tier 4 |
Step 6: Interpretation
The results highlight several non-obvious truths:
- Recovery capability outranks detection
- Infrastructure hygiene outranks user behavior
- Controls that look impressive may rank low
- Controls that feel boring often dominate
This is basically the mathematical expression of attacker intent.
Why the Calculation Matters
Without explicit scoring:
- prioritization becomes opinion
- decisions become political
- trade offs remain implicit
ACDP forces those trade-offs into the open.
If you cannot explain your priorities numerically, you are not prioritizing: you are rationalizing
Closing Thoughts
Often times security failures are caused not by missing controls, but by misaligned priorities.
ACDP was developed to address this misalignment by shifting the focus from technique coverage to attacker intent, and from abstract risk to tangible impact. Its value lies in deliberate selection.
Used correctly, ACDP does not replace existing frameworks, but sharpens them by forcing uncomfortable but necessary decisions.
This methodology is intentionally opinionated!
If you have any feedback or questions, please feel free to contact me by email.
I welcome criticism and feedback!